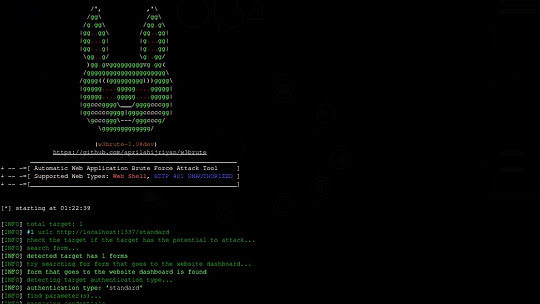
w3brute is an open source penetration testing tool that automates attacks directly to the website’s login page. w3brute is also supported for carrying out brute force attacks on all websites.
Features
- Scanner:
w3brute has a scanner feature that serves to support the bruteforce attack process. this is a list of available scanners:
- automatically detects target authentication type.
- admin page scanner.
- SQL injection scanner vulnerability.
- Attack Method:
w3brute can attack using various methods of attack. this is a list of available attack methods:
- SQL injection bypass authentication
- mixed credentials (username + SQL injection queries)
- Support:
- multiple target
- google dorking
- a list of supported web interface types to attack:
- web shell
- HTTP 401 UNAUTHORIZED (Basic and Digest)
- create file results brute force attack. supported file format type:
- CSV (default)
- HTML
- SQLITE3
- custom credentials (username, password, domain) (supported zip file)
- custom HTTP requests (User-Agent, timeout, etc)
- and much more…
Installation
You can download the latest version of the tarball file here or zipball here. If you have installed the git package, you can clone the Git repository in a way, as below:
git clone https://github.com/aprilahijriyan/w3brute.gitw3brute can be run with Python version 2.6.x or 2.7.x on all platforms.
Usage
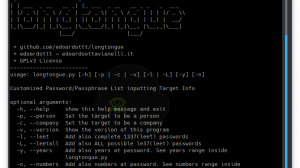
To get all list of options on w3brute tool:
python w3brute.py -hExamples:
# basic usage
$ python w3brute.py -t http://www.example.com/admin/login.php
# look for the admin page
$ python w3brute.py -t http://www.example.com/ --admin
# uses a password file zip list. (syntax => <path><;filename>[:password])
$ python w3brute.py -t http://www.example.com/ --admin -u admin -p /path/to/file.zip;filename.txt # (if the file is encrypted: /path/to/file.zip;filename.txt:password)
# slice the password from the list. (syntax => <start>[:stop][:step])
$ python w3brute.py -t http://www.example.com/ --admin -u admin -sP 20000Video
[youtube https://www.youtube.com/watch?v=u4mi-cfRfGA&w=560&h=315]
Links
- Download: .tar.gz or .zip
- Issue tracker: https://github.com/aprilahijriyan/w3brute/issues


















Add Comment