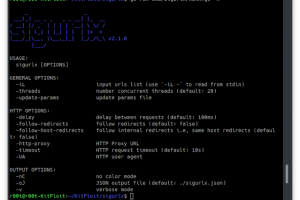
[sc name=”ad_1″] sigurlx a web application attack surface mapping tool, it does …: Categorize URLs URLs’ categories: > endpoint >...
Tag - Attack
[sc name=”ad_1″] Go365 is a tool designed to perform user enumeration* and password guessing attacks on organizations that use Office365 (now/soon...
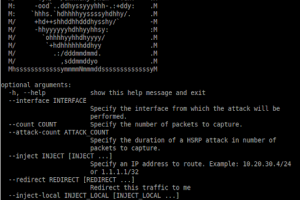
[sc name=”ad_1″] Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic...
[sc name=”ad_1″] Leonidas is a framework for executing attacker actions in the cloud. It provides a YAML-based format for defining cloud attacker...
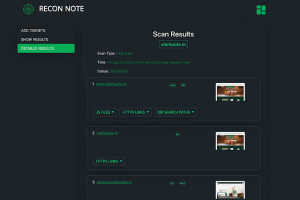
[sc name=”ad_1″] Web Application Security Recon Automation Framework It takes user input as a domain name and maximize the attack surface area by...
[sc name=”ad_1″] GWTMap is a tool to help map the attack surface of Google Web Toolkit (GWT) based applications. The purpose of this tool is to...
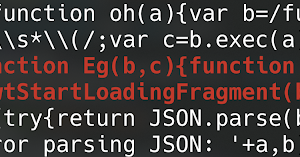
[sc name=”ad_1″] jwt-hack is tool for hacking / security testing to JWT. Supported for En/decoding JWT, Generate payload for JWT attack and very...
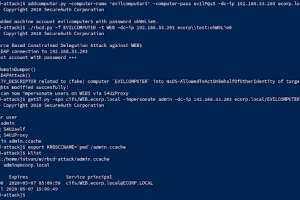
[sc name=”ad_1″] Abusing Kerberos Resource-Based Constrained Delegation TL;DR This repo is about a practical attack against Kerberos Resource-Based...
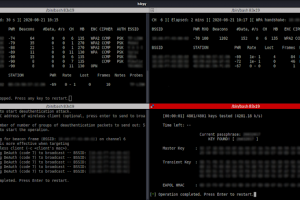
[sc name=”ad_1″] h4rpy is an automated WPA/WPA2 PSK attack tool, wrapper of aircrack-ng framework. h4rpy provides clean interface for automated...
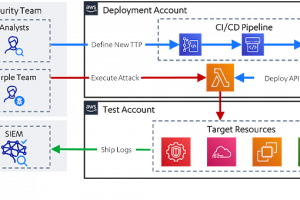
[sc name=”ad_1″] Defending enterprise networks against attackers continues to present a difficult challenge for blue teams. Prevention has fallen...