[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
Tag - toolkit
[sc name=”ad_1″] dnsx is a fast and multi-purpose DNS toolkit allow to run multiple probers using retryabledns library, that allows you to perform...
[sc name=”ad_1″] Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic...
[sc name=”ad_1″] NFCGate is an Android application meant to capture, analyze, or modify NFC traffic. It can be used as a researching tool to...
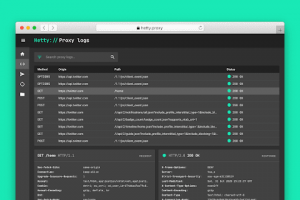
[sc name=”ad_1″] Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp...
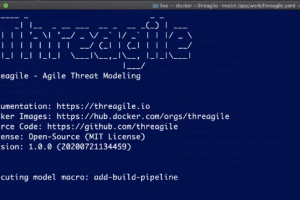
[sc name=”ad_1″] Threagile (see for more details) is an open-source toolkit for agile threat modeling: It allows to model an architecture with its...
[sc name=”ad_1″] GWTMap is a tool to help map the attack surface of Google Web Toolkit (GWT) based applications. The purpose of this tool is to...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] TaoWu(檮杌) is a CobaltStrike toolkit. All the scripts are gathered on the Internet and slightly modified by myself. You can use it...
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right...