[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
Tag - Techniques
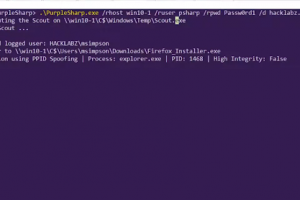
[sc name=”ad_1″] Defending enterprise networks against attackers continues to present a difficult challenge for blue teams. Prevention has fallen...
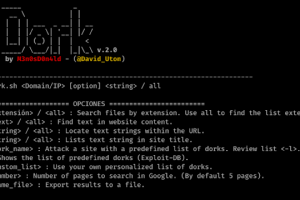
[sc name=”ad_1″] uDork is a script written in Bash Scripting that uses advanced Google search techniques to obtain sensitive information in files...
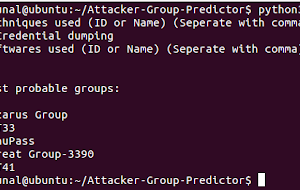
[sc name=”ad_1″] The tool predicts attacker groups from techniques and softwares used. It searches based on the MITRE ATT&CK framework How it...
[sc name=”ad_1″] In this malware, are used some techniques to try bypass the AVs, VMs, and Sandboxes, with only porpuse to learning more. I’m...
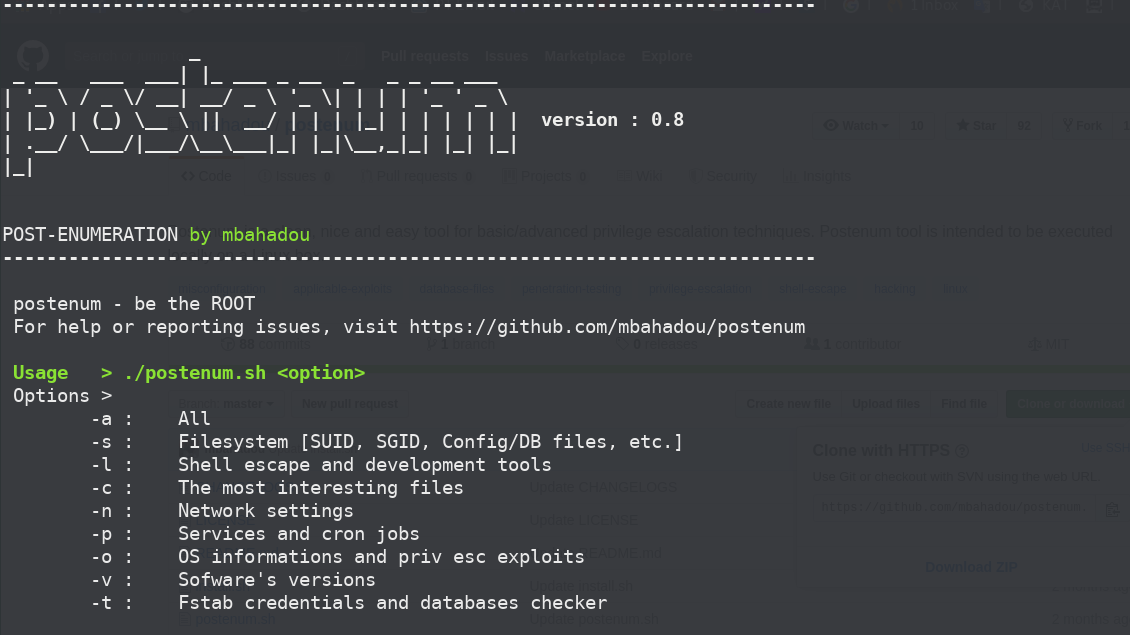
[sc name=”ad_1″] Postenum is a clean, nice and easy tool for basic/advanced privilege escalation vectors/techniques. Postenum tool is intended to...