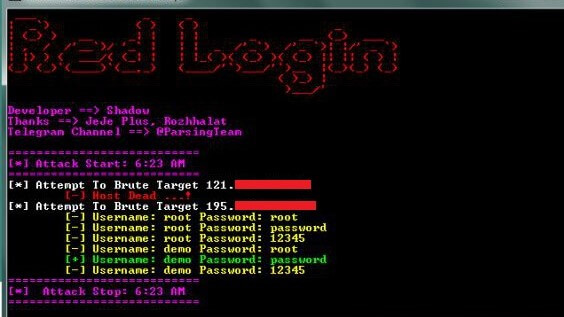
Red Login: SSH Brute-force Tools. Features: High speed and precision CLI ( Console based ) Run the arbitrary command after the attack is successful ( Default...
Tag - ssh
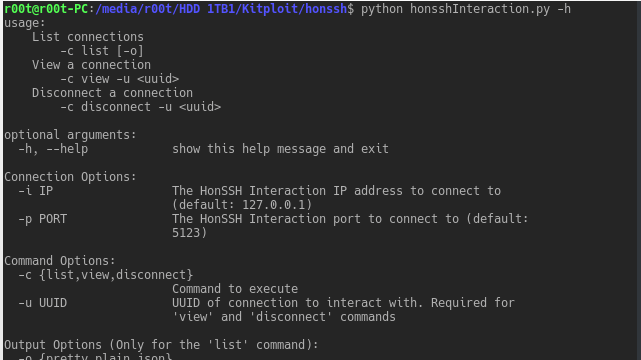
HonSSH is a high-interaction Honey Pot solution. HonSSH will sit between an attacker and a honey pot, creating two separate SSH connections between them...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
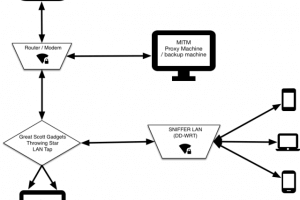
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
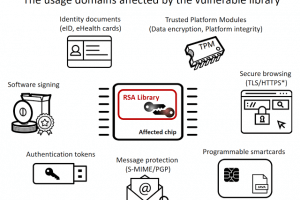
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...
About Getting default credentials added to commercial scanners is often difficult and slow. changeme is designed to be simple to add new credentials without...
Programming Languages : BASH RUN root@ismailtasdelen:~# bash ./anti-ddos.sh Cloning an Existing Repository ( Clone with HTTPS ) git clone Cloning an Existing...
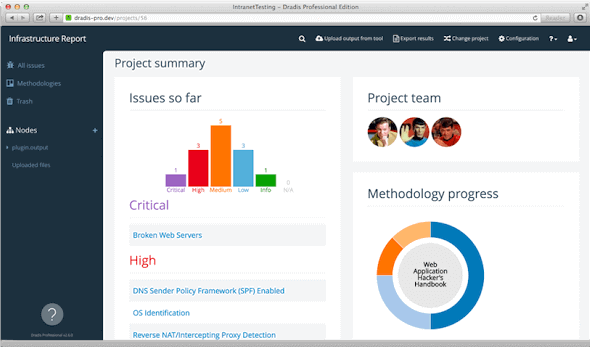
Dradis is an open-source collaboration framework, tailored to InfoSec teams. Goals Share the information effectively. Easy to use, easy to be adopted...