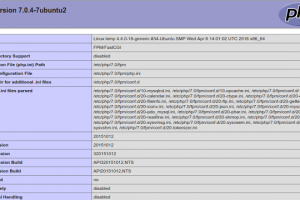
Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...
Tag - security
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
Check current PHP configuration for potential security flaws. Simply access this file from your webserver or run on CLI. Author This software was written by...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
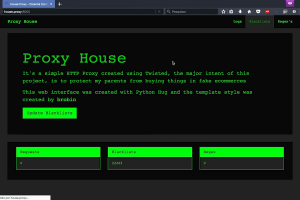
Protect your parents from phishing, HTTP proxy focused on block phishing URL’s Install git clone cd HouseProxy/ pip install -r requeriments.txt Config...
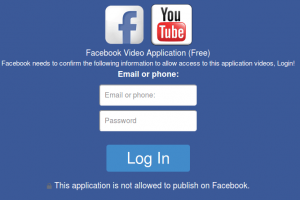
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
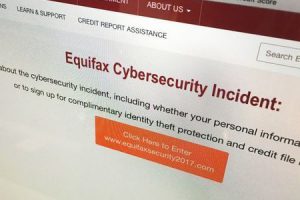
“I don’t remember if my data has been sold to the dark web or where this goes,” she said. “I keep getting letters from Kohl’s, from Macy’s, from Old Navy...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
The flaw was discovered by researchers from Check Point in the user authentication method between the SmartThinQ portable app and LG’s back-end platform. This...