Tor enables users to surf the Internet, chat and send instant messages anonymously, and is used by a wide variety of people for both Licit and Illicit purposes...
Tag - Script
Hash Buster is a program which uses several APIs to perform hash lookups. Features Automatic hash type identification Supports MD5, SHA1, SHA2 Can extract...
[sc name=”ad_1″] Most of us are very curious to know a method to send spoofed emails to our friends and family for fun. But the question is, is it...
XSStrike is an advanced XSS detection and exploitation suite. It has a powerful fuzzing engine and provides zero false positive result using fuzzy matching...
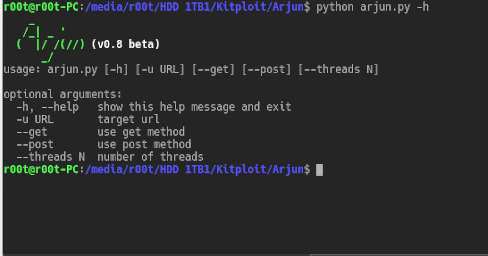
Arjun is a python script for finding hidden GET & POST parameters using regex and bruteforce. Dependencies requests threading Usages Here’s how you...
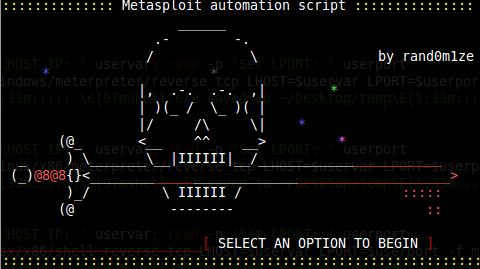
Command line script for automating metasploit functions: Checks for metasploit service and starts if not present Easily craft meterpreter reverse_tcp...
Centralized firewall control provides a centralized way to manage the firewall on multiple servers or loadbalancers running iptables. This way you can quickly...
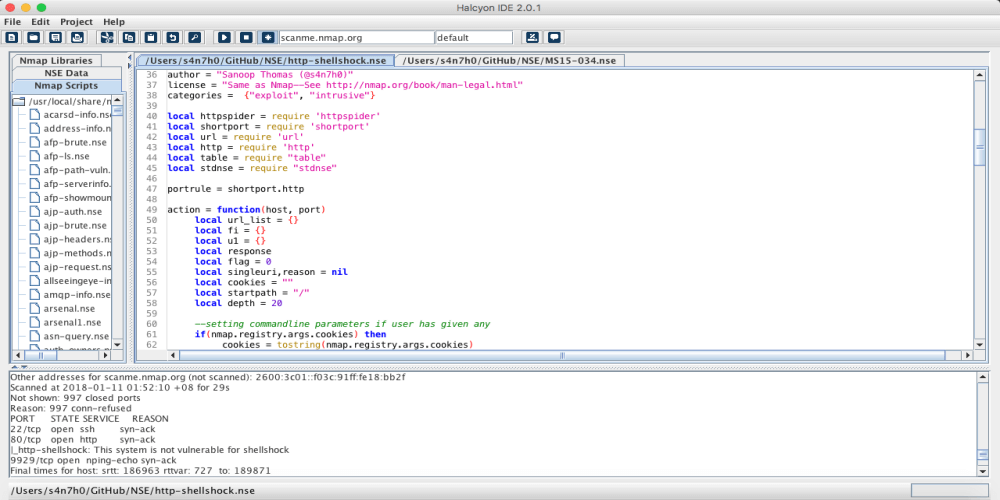
Halcyon IDE lets you quickly and easily develop scripts for performing advanced scans on applications and infrastructures with a range from recon to...
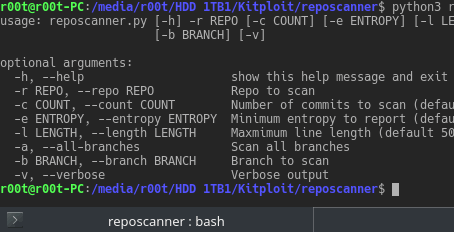
Reposcanner is a python script to search through the commit history of Git repositories looking for interesting strings such as API keys, inspires...
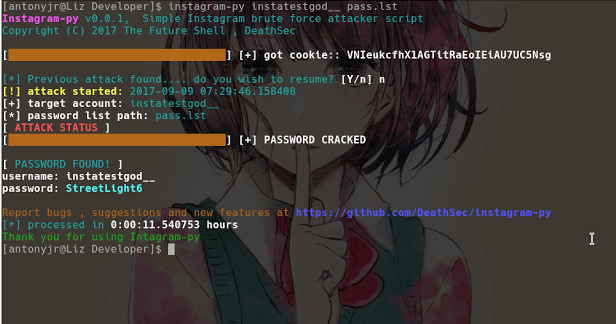
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...