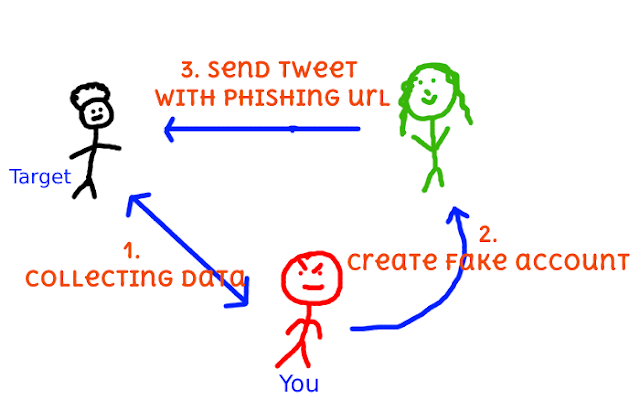
How it works? 1- Collect data from target’s twitter account 2- Find target’s friend and copy her/him account 3- Generate tweet automatically with...
Tag - phishing
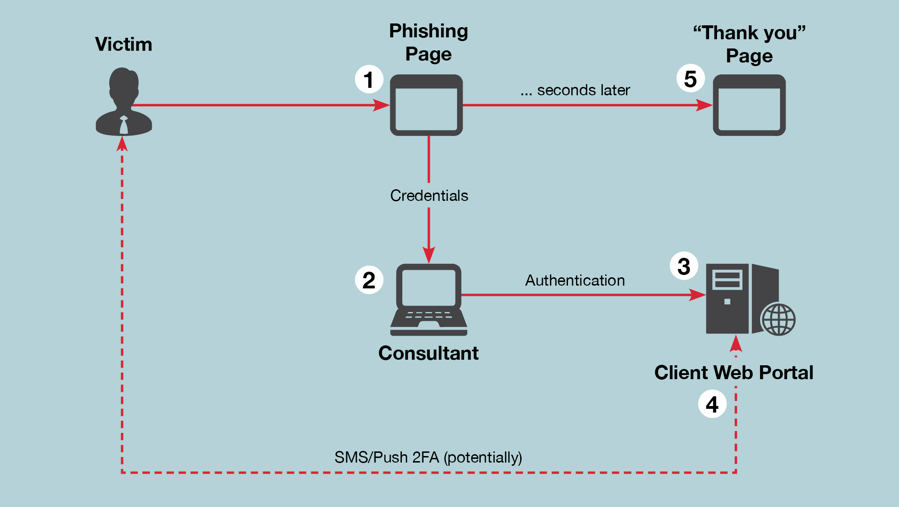
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
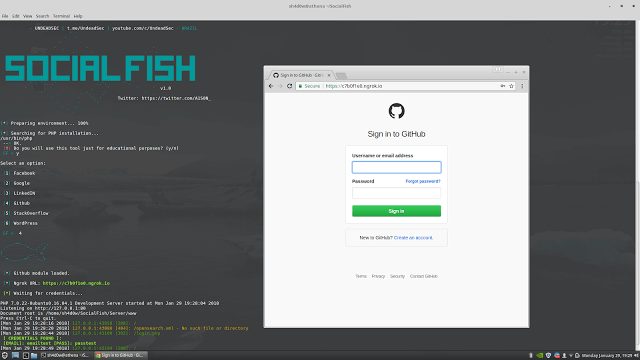
Ultimate phishing tool with Ngrok integrated. PREREQUISITES Python 2.7 Wget from Python PHP sudo TESTED ON Kali Linux – Rolling Edition Linux Mint...
Ultimate phishing tool with Ngrok integrated. PREREQUISITES Python 2.7 Wget from Python PHP TESTED ON Kali Linux – ROLLING EDITION CLONE git clone...
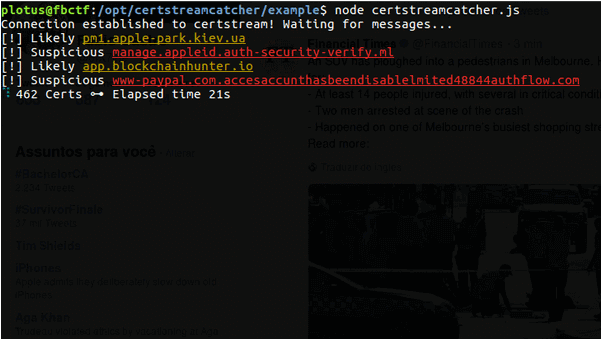
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...
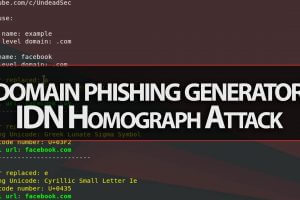
Hey Guys, In this video i show you a great tool for unicode domain phishing generation for IDN Homograph Attack. EvilURL: CLONE git clone RUNNING cd EvilURL...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
An unicode domain phishing generator for IDN Homograph Attack. CLONE git clone RUNNING cd EvilURL python evilurl.py PREREQUISITES python 2.7 TESTED ON Kali...
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...