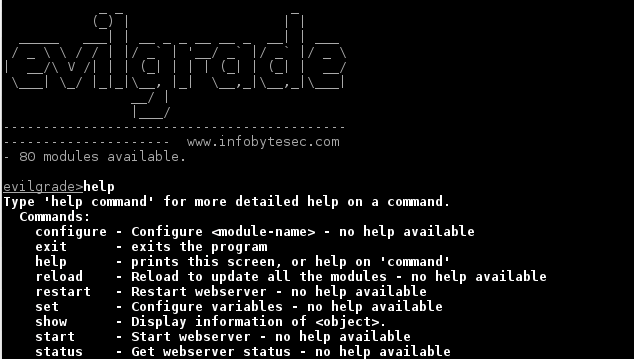
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
Tag - metasploit
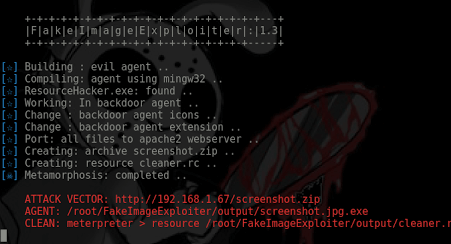
This module takes one existing image.jpg and one payload.ps1 (input by user) and builds a new payload (agent.jpg.exe) that if executed it will trigger the...
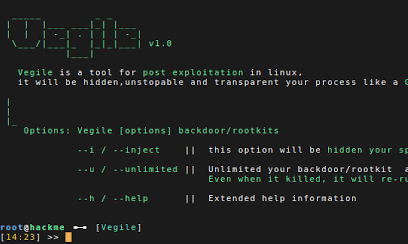
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...
Simple TCP reverse shell written in Go. It uses TLS to secure the communications, and provide a certificate public key fingerprint pinning feature, preventing...
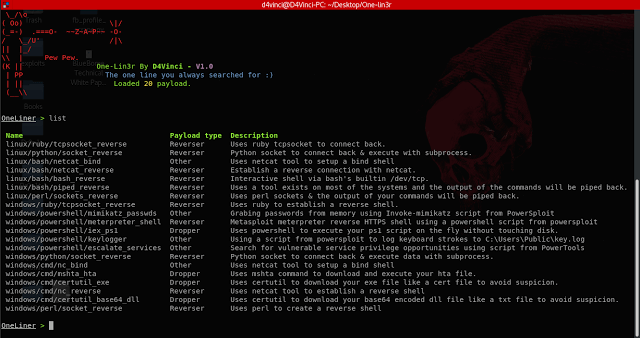
One-Lin3r is simple and light-weight framework inspired by the web-delivery module in Metasploit. It consists of various one-liners that aids in penetration...
NXcrypt is a polymorphic ‘python backdoors’ crypter written in python by Hadi Mene (h4d3s) . The output is fully undetectable. NXcrypt can inject...
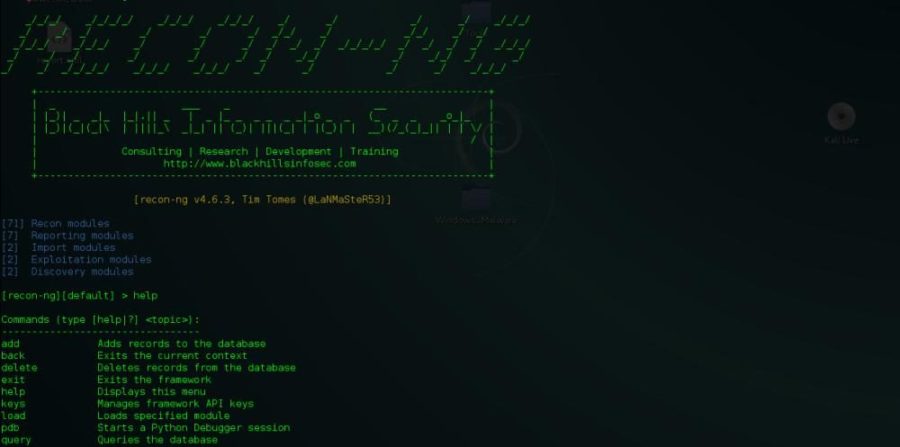
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience...
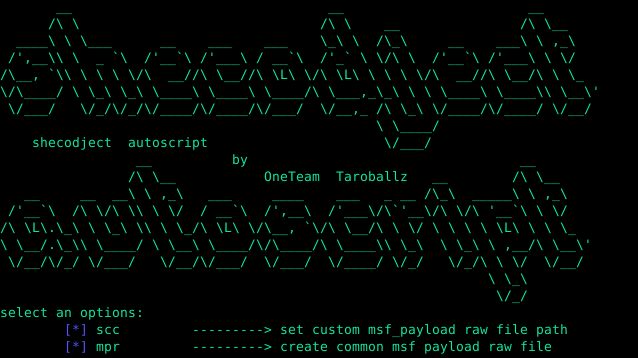
shecoject is a tool written in python3, which can be used to package raw metasploit-generated raw files directly into the pyinstaller package or you can use...
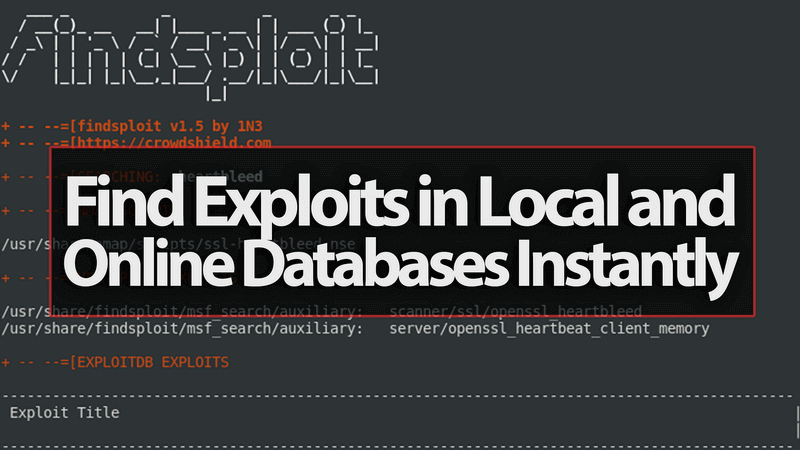
Findsploit is a simple bash script to quickly and easily search both local and online exploit databases. Findsploit: Installation: git clone cd Findsploit...
What this tool does is taking a file (any type of file), encrypt it, and embed it into an HTML file as ressource, along with an automatic download routine...