[sc name=”ad_1″] Hey Guys, In this video i show you how to Embed a Metasploit Payload in an Original .Apk File. Normally we have to install the...
Tag - metasploit
Mass mailer is commonly used to send a phishing page link to the e-mail ID of the target. The attacker needs to be aware of the e-mail harvester technique to...
Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber’s powershell attacks...
Sn1per is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Features: Automatically collects basic...
TopHat is inspired by metasploit’s capabilties of meterpreter however it was coded to generate a undetected encrypted backdoor using python. Usage:...
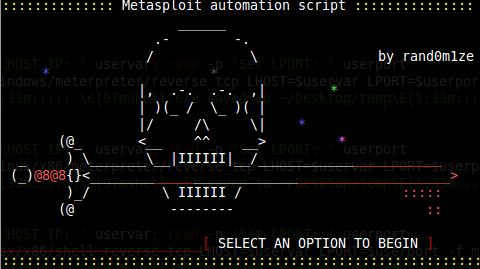
Command line script for automating metasploit functions: Checks for metasploit service and starts if not present Easily craft meterpreter reverse_tcp...
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of...
The script will use msfvenom (metasploit) to generate shellcode in diferent formats ( c | python | ruby | dll | msi | hta-psh ) injects the shellcode generated...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
WPSploit is intended for Penetration Testers who audit WordPress plugins or developers who wish to audit their own WordPress plugins. It checks for: Cross-Site...