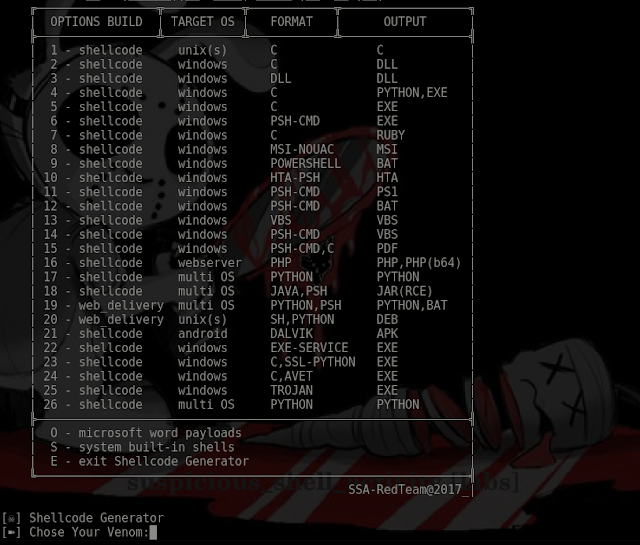
The script will use msfvenom (metasploit) to generate shellcode in diferent formats ( c | python | ruby | dll | msi | hta-psh ) injects the shellcode generated into one template (example: python) “the python funtion will execute the shellcode into ram” and uses compilers like gcc (gnu cross compiler) or mingw32 or pyinstaller to build the executable file, also starts a multi-handler to recive the remote connection (shell or meterpreter session).
HOW DO I DELIVER MY PAYLOADS TO TARGET HOST ?
venom (malicious_server) was build to take advantage of apache2 webserver to deliver payloads (LAN) using a fake webpage writen in html that takes advantage of <iframe> <meta-http-equiv> or “<form>” tags to be hable to trigger payload downloads, the user just needs to send the link provided to target host.
“Apache2 (malicious url) will copy all files needed to your webroot”
DEPENDENCIES
- Zenity
- Metasploit
- GCC (compiler)
- Pyinstaller (compiler)
- mingw32 (compiler)
- pyherion.py (crypter)
- wine (emulator)
- PEScrambler.exe (PE obfuscator)
- apache2 (webserver)| winrar (wine)
- vbs-obfuscator (obfuscator)
- avet (Daniel Sauder)
- shellter (KyRecon)
- ettercap (MitM + DNS_Spoofing)
- encrypt_PolarSSL (AES crypter)
“venom.sh will download/install all dependencies as they are needed”
Adicionally was build venom-main/aux/setup.sh to help you install all venom framework dependencies (metasploit as to be manually installed).
DOWNLOAD/INSTALL
1° - Download framework from github
git clone https://github.com/r00t-3xp10it/venom.git
2° - Set files execution permitions
cd venom-main
sudo chmod -R +x *.sh
sudo chmod -R +x *.py
3° - Install dependencies
cd aux
sudo ./setup.sh
4° - Run main tool
sudo ./venom.shFramework Main Menu
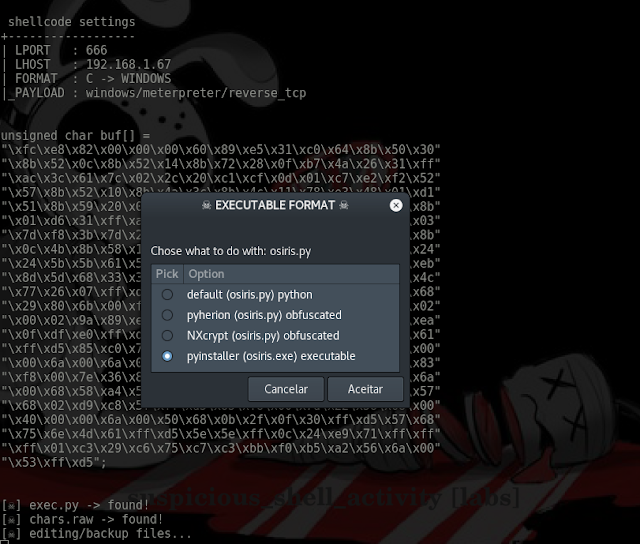
[ Build 4 ] python/pyinstaller – osiris.exe
Build 4 Work floow: Build shellcode in C language, embebbed into one python template and compiled to exe by pyinstaller = osiris.exe






















Add Comment