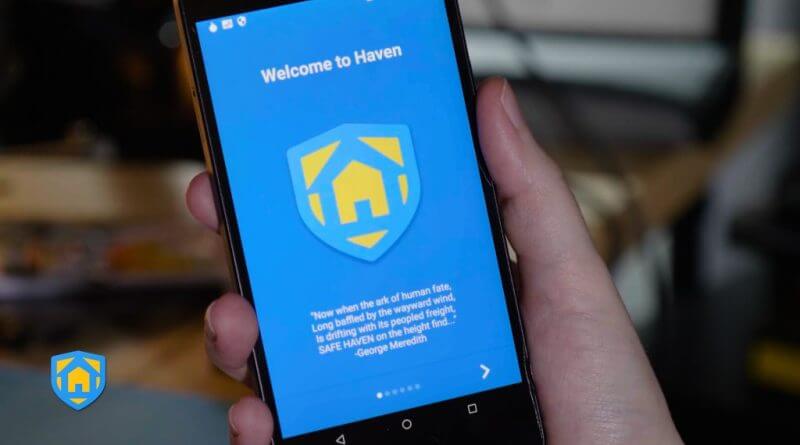
Snowden told Moudeina that he was operating on an app that could turn a mobile device into a kind of motion sensor in form to notify you when your things are...
Tag - mac
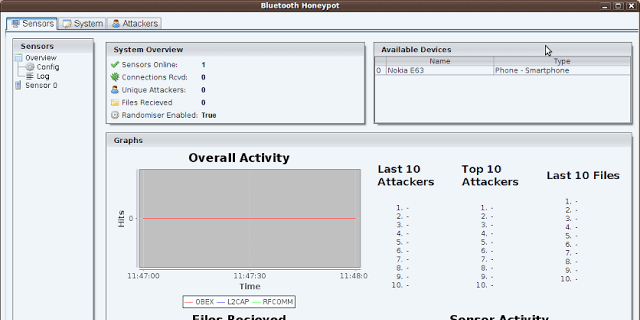
This code is from a University Project written in 2010. This is a newer version of the code than is on Google Code. Bluepot is a Bluetooth Honeypot written in...
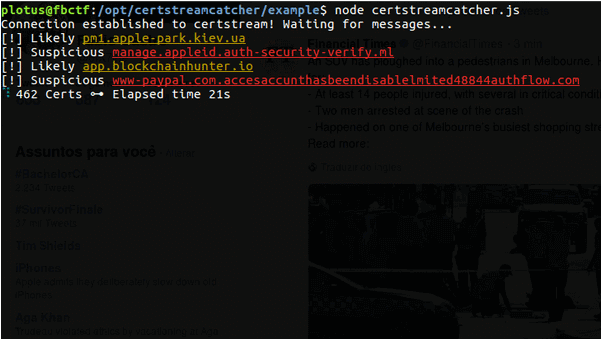
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
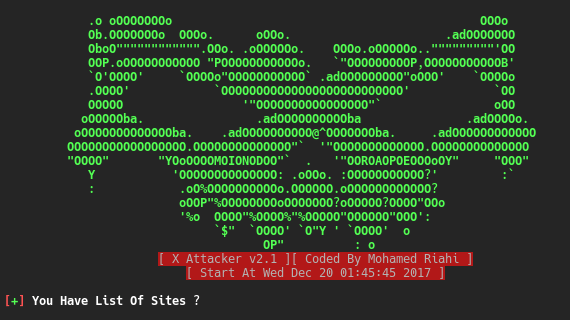
XAttacker is a Website Vulnerability Scanner & Auto Exploiter developed by Mohamed Riahi Auto Cms Detect [1] WordPress : [+] Adblock Blocker [+] WP All...
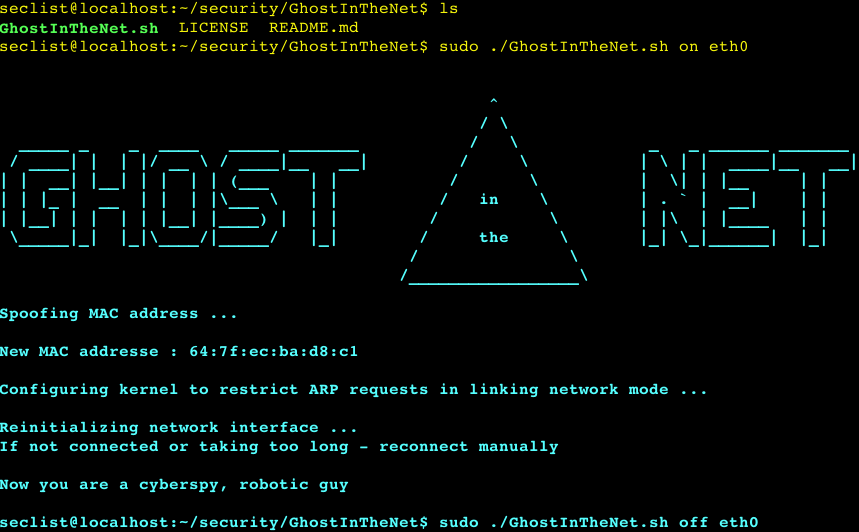
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
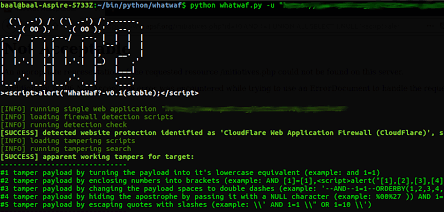
WhatWaf is an advanced firewall detection tool who’s goal is to give you the idea of “There’s a WAF?”. WhatWaf works by detecting a...
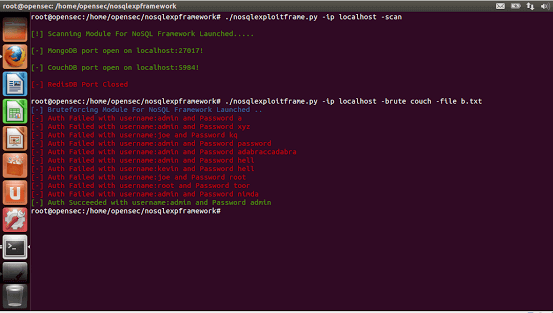
A FrameWork For NoSQL Scanning and Exploitation Framework Authored By Francis Alexander. Added Features: First Ever Tool With Added Support For...
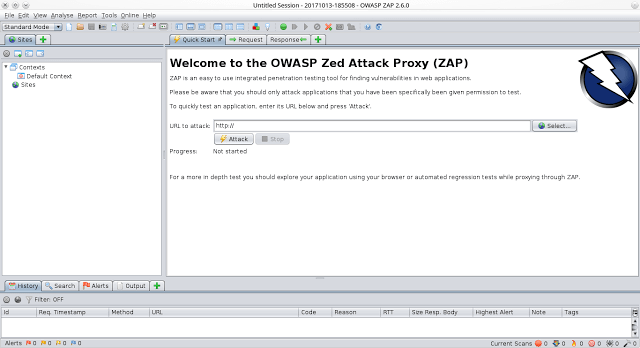
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It...
dirsearch is a simple command line tool designed to brute force directories and files in websites. Operating Systems supported Windows XP/7/8/10 GNU/Linux...
Droidefense (originally named atom: analysis through observation machine)* is the codename for android apps/malware analysis/reversing tool. It was built...