BruteSpray takes nmap GNMAP/XML output and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard...
Tag - linux
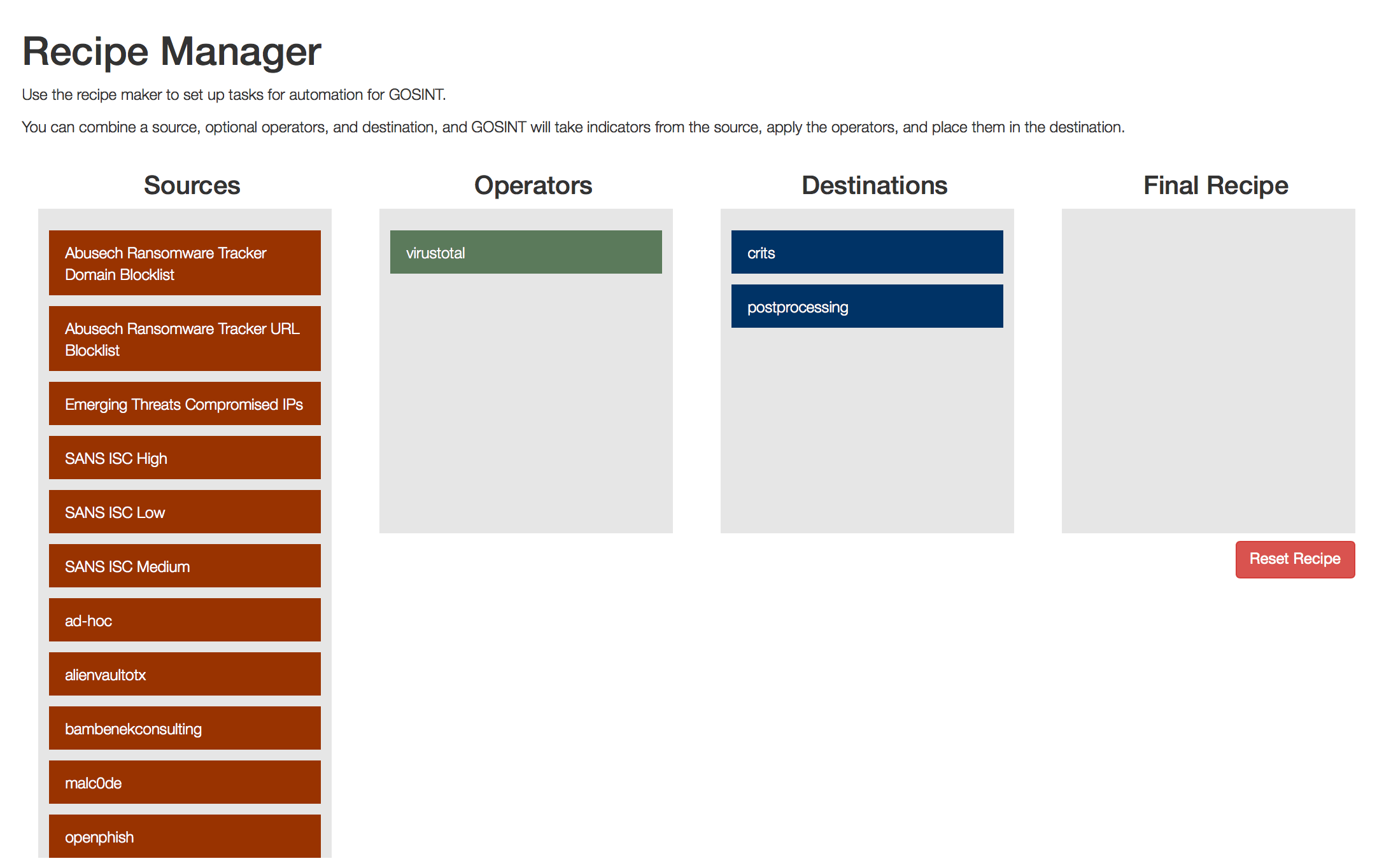
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...
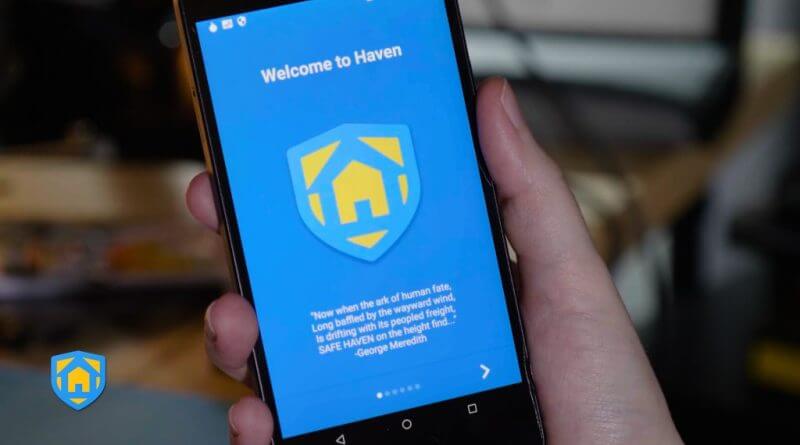
Snowden told Moudeina that he was operating on an app that could turn a mobile device into a kind of motion sensor in form to notify you when your things are...
Archery is an opensource vulnerability assessment and management tool which helps developers and pentesters to perform scans and manage vulnerabilities...
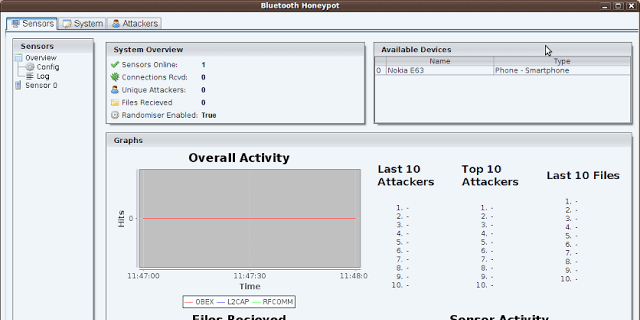
This code is from a University Project written in 2010. This is a newer version of the code than is on Google Code. Bluepot is a Bluetooth Honeypot written in...
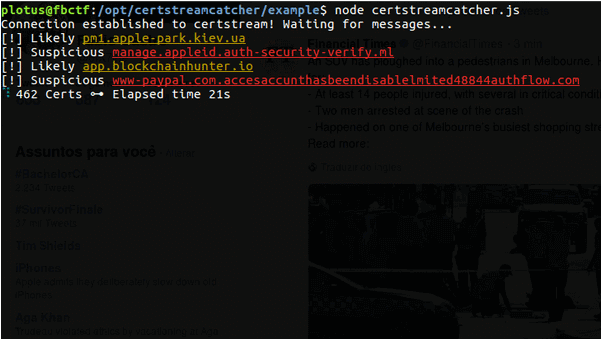
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
A script for installing and automatically configuring DNSCrypt on Linux-based systems. Description DNSCrypt is a protocol for securing communications between a...
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
The corporation says that version 390 of its GPU video driver will be the last to carry 32-bit platforms. “Later driver release reports will not operate, nor...