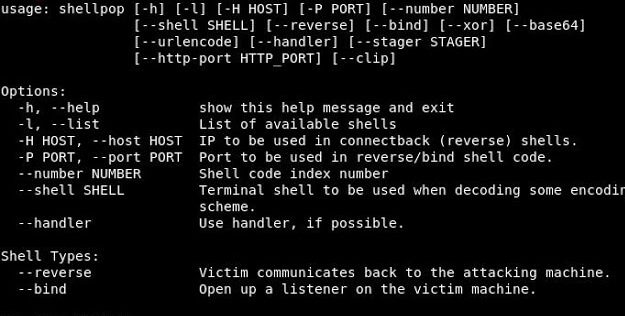
Pop shells like a master Shell pop is all about popping shells. With this tool you can generate easy and sofisticated reverse or bind shell commands to help...
Tag - linux
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
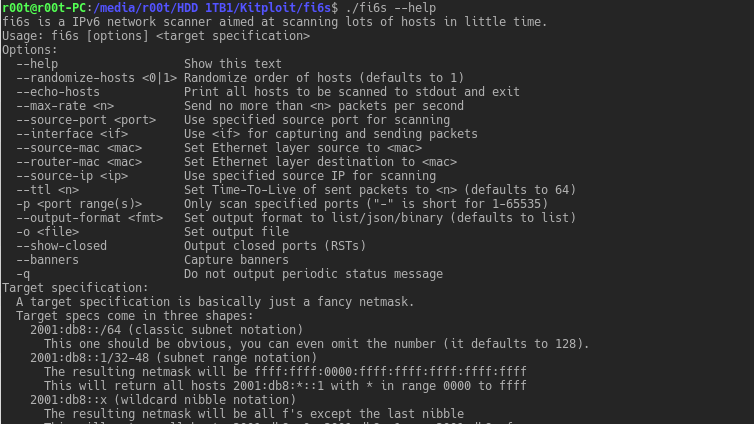
fi6s is a IPv6 port scanner designed to be fast. This is achieved by sending and processing raw packets asynchronously. The design and goal is pretty similar...
The single most common causes of a broken Kali Linux installation are following unofficial advice, and particularly arbitrarily populating the system’s sources...
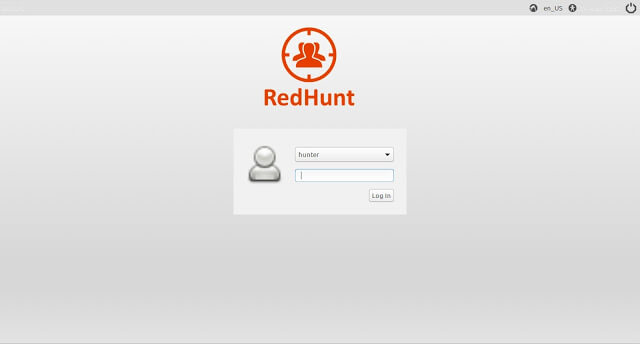
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
Red Team Arsenal is a web/network security scanner which has the capability to scan all company’s online facing assets and provide an holistic security view of...
Parat is a simple remote administration tool(RAT) written in python. Features Fully UnDetectable(FUD) Compatible with Telegram messanger Bypass windows User...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
This is Part 2 of Linux Basics In this Part we will talk about your first steps with linux. Logging In and Out: The Linux system distinguishes between...
[sc name=”ad_1″] Hey Guys, In this video i show you how to Embed a Metasploit Payload in an Original .Apk File. Normally we have to install the...