[sc name=”ad_1″] A graphical interface to use information security tools by the browser. Getting Started Kali Linux Tools Interface is a graphical...
Tag - Information
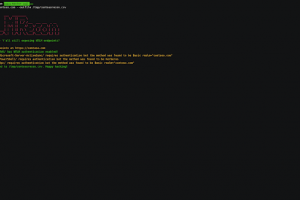
[sc name=”ad_1″] A fast and flexible NTLM reconnaissance tool without external dependencies. Useful to find out information about NTLM endpoints...
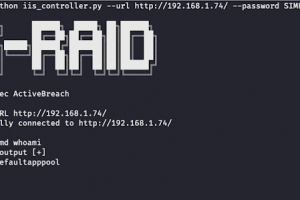
[sc name=”ad_1″] IS Raid is a native IIS module that abuses the extendibility of IIS to backdoor the web server and carry out custom actions...
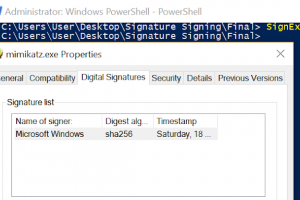
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
[sc name=”ad_1″] GitMonitor is a Github scanning system to look for leaked sensitive information based on rules. I know that there are a lot of...
[sc name=”ad_1″] ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors. It will...
[sc name=”ad_1″] Project iKy is a tool that collects information from an email and shows results in a nice visual interface. Visit the Gitlab Page...
[sc name=”ad_1″] Semi-Automated Cyber Threat Intelligence (ACT) is a research project led by mnemonic as with contributions from the University of...
[sc name=”ad_1″] FOCA (Fingerprinting Organizations with Collected Archives) FOCA is a tool used mainly to find metadata and hidden information in...
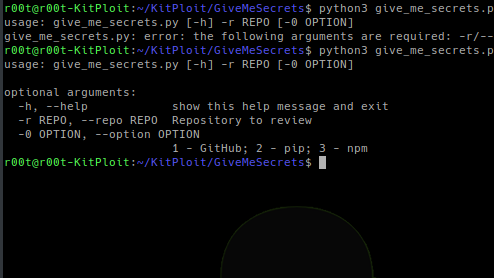
[sc name=”ad_1″] Use regular expressions to get sensitive information from a given repository (GitHub, pip or npm). Dependencies You only need to...