When it comes to security updates, Android is a real mess. Even after Google timely rolls out security patches for its Android platform, a major part of the...
Tag - how to hack
Cybersecurity firm FireEye claims to have discovered evidence that proves the involvement of a Russian-owned research institute in the development of the...
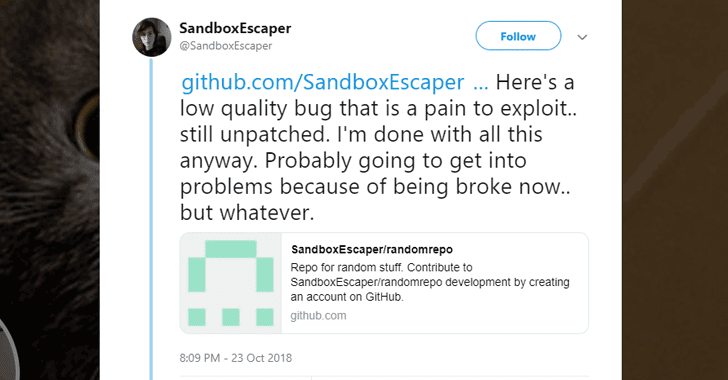
A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
MAC Changer is an utility that makes the maniputation of MAC addresses of network interfaces easier. A media access control (Mac) address of a device is a...