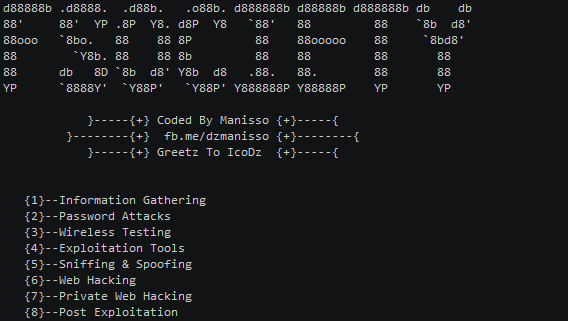
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
Tag - hacking
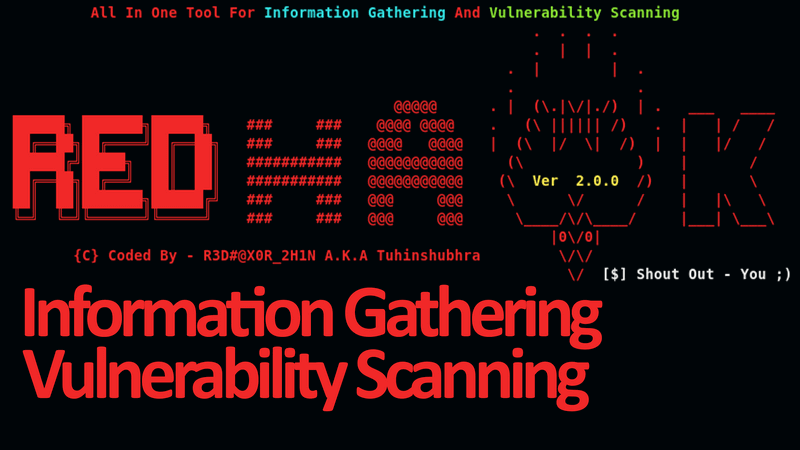
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
MoneyTaker hackers, A group of Russian hackers, has been laying waste to banks internationally and locally. In the past 18 months, this group has stolen a...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...
Denis Sinegubko (a security researcher from Sucuri) has discovered a new wave of the known malware wp-vcd that injects malicious WordPress admin users into...
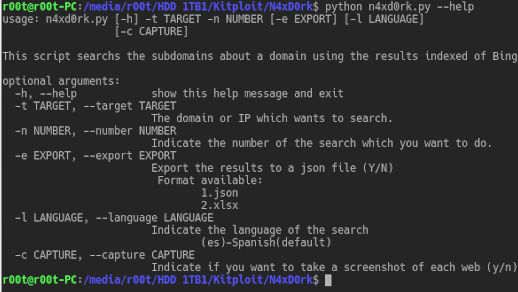
Listing subdomains about the main domain using the technique called Hacking with search engines. Usage usage: n4xd0rk.py [-h] [-d DOMAIN] [-i IP] -o OPTION -n...