Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
Tag - Forensics
Programming Languages : BASH RUN root@ismailtasdelen:~# bash ./anti-ddos.sh Cloning an Existing Repository ( Clone with HTTPS ) git clone Cloning an Existing...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
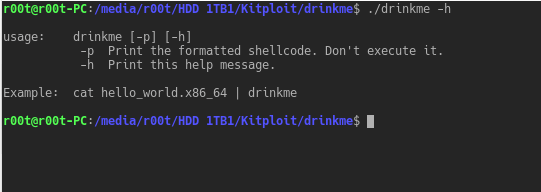
drinkme is a shellcode test harness. It reads shellcode from stdin and executes it. This allows pentesters to quickly test their payloads before deployment...
Security researchers from AccessNow have discovered a new Facebook phishing scam that can also fool a professional technical user into falling victim to this...
Reverse Engineer .NET Assemblies dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor (and more)...
The project is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. Note: The...
Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...
The Port Scan Attack Detector psad is a lightweight system daemon written in is designed to work with Linux iptables/ip6tables/firewalld firewalling code to...
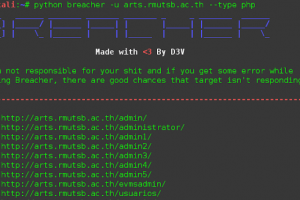
A script to find admin login pages and EAR vulnerabilites. Features Multi-threading on demand Big path list (798 paths) Supports php, asp and html extensions...