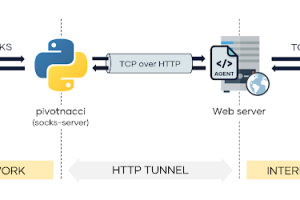
[sc name=”ad_1″] Pivot into the internal network by deploying HTTP agents. Pivotnacci allows you to create a socks server which communicates with...
Tag - connections
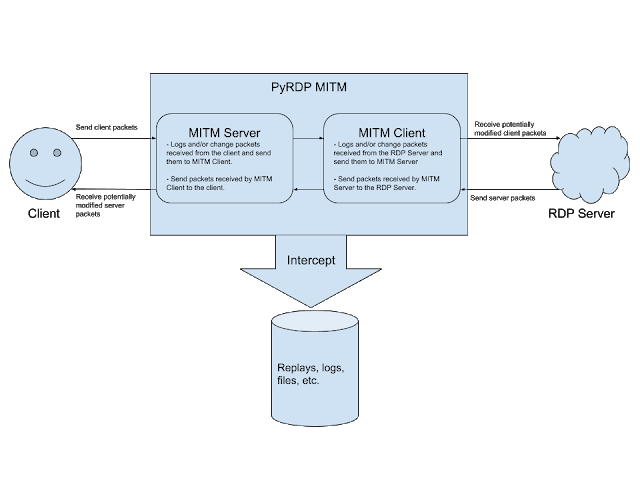
[sc name=”ad_1″] PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library. It features a few tools: RDP Man-in-the...
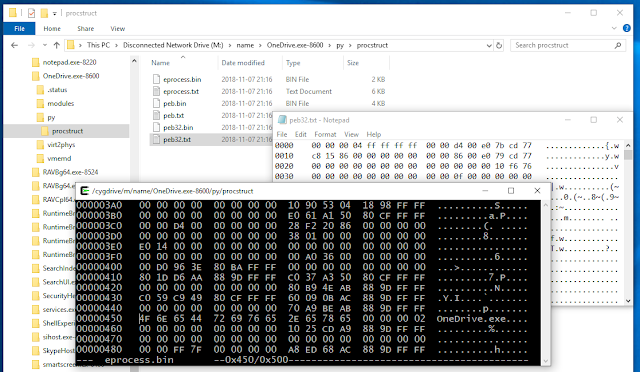
[sc name=”ad_1″] The Memory Process File System is an easy and convenient way of accessing physical memory as files a virtual file system. Easy...
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
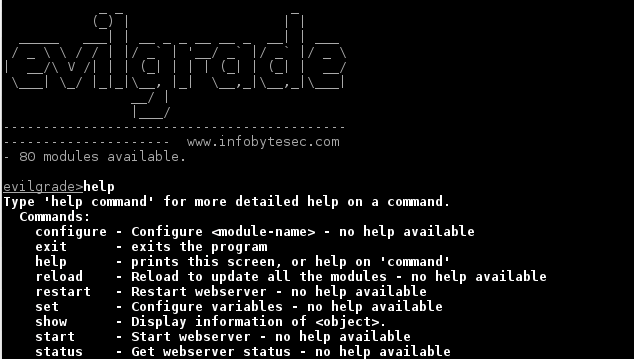
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
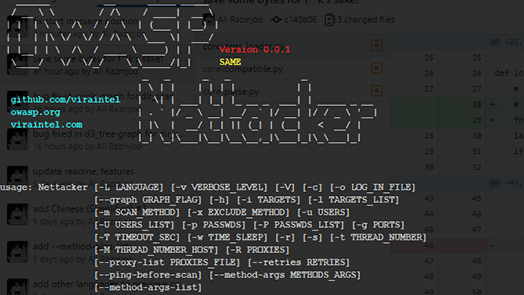
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
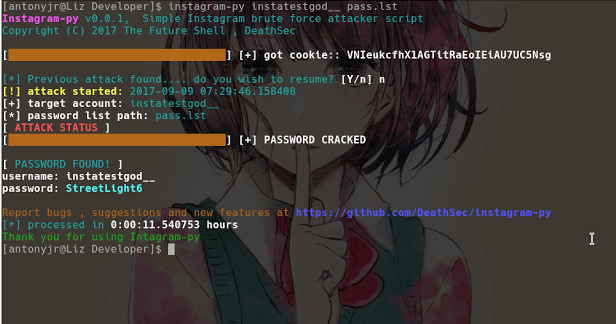
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
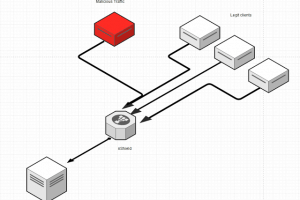
An Easy and Simple Anti-DDoS solution for VPS,Dedicated Servers and IoT devices based on iptables. Requirements Linux System with python, iptables Nginx (Will...
DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...