[sc name=”ad_1″] Static analysis to search for vulnerabilities in WordPress plugins. __ ____________ ___ ___ __ / / ______ / | __ __ _____/ |_...
Search Results For - vulnerabilities
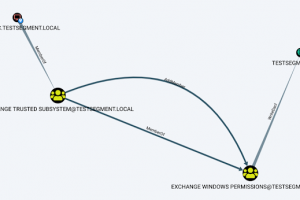
[sc name=”ad_1″] Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a...
[sc name=”ad_1″] Without practice, theory is dead. Applied knowledge is essential in any area, especially in cybersecurity, and practice is the...
[sc name=”ad_1″] A small contribution to community 🙂 We use all these tools in security assessments and in our vulnerability monitoring service...
[sc name=”ad_1″] Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native...
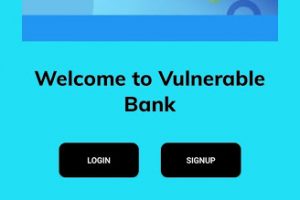
[sc name=”ad_1″] Damn Vulnerable Bank Android Application aims to provide an interface for everyone to get a detailed understanding with internals...
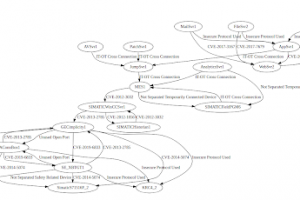
[sc name=”ad_1″] This prototype identifies security risk sources (i.e., threats and vulnerabilities) and types of attack consequences based on...
[sc name=”ad_1″] A (coverage-)guided fuzzer for dynamic language interpreters based on a custom intermediate language (“FuzzIL”) which...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] Based on pywebfuzz, Py3webfuzz is a Python3 module to assist in the identification of vulnerabilities in web applications, Web...