Use open source tools and network intelligence to help organizations with attack surface discovery and identification of security vulnerabilities...
Search Results For - vulnerabilities
All major web browsers, including Google Chrome, Apple Safari, Microsoft Edge, Internet Explorer, and Mozilla Firefox, altogether today announced to soon...
Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
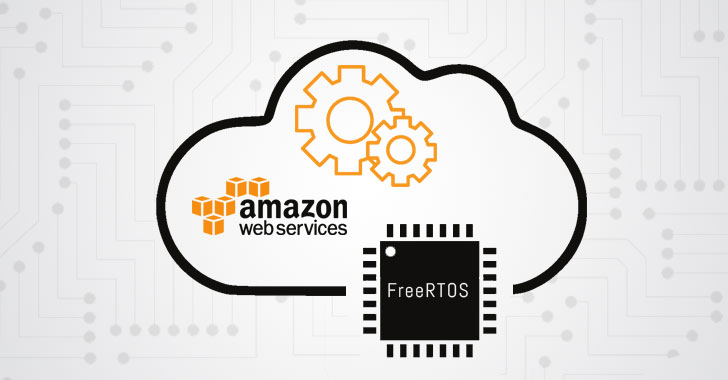
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Microsoft Windows built-in anti-malware tool, Windows Defender, has become the very first antivirus software to have the ability to run inside a sandbox...
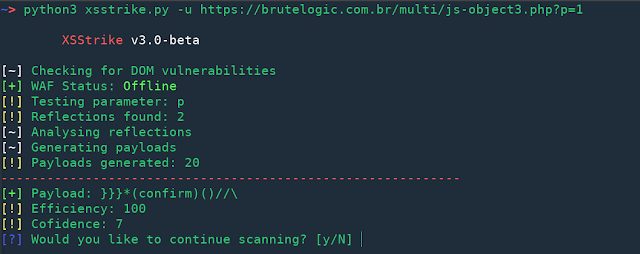
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract...
When it comes to security updates, Android is a real mess. Even after Google timely rolls out security patches for its Android platform, a major part of the...
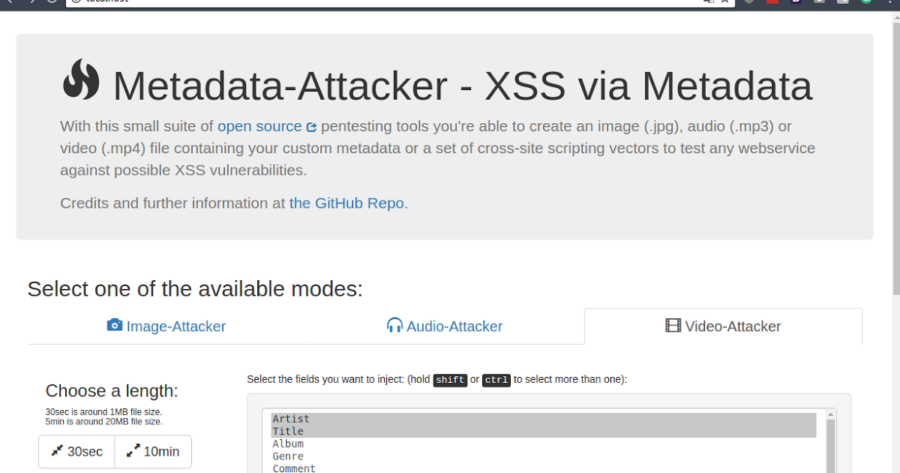
Metadata-Attacker or a set of cross-site scripting vectors to test any webservice against possible XSS vulnerabilities when displaying unfiltered meta datWith...
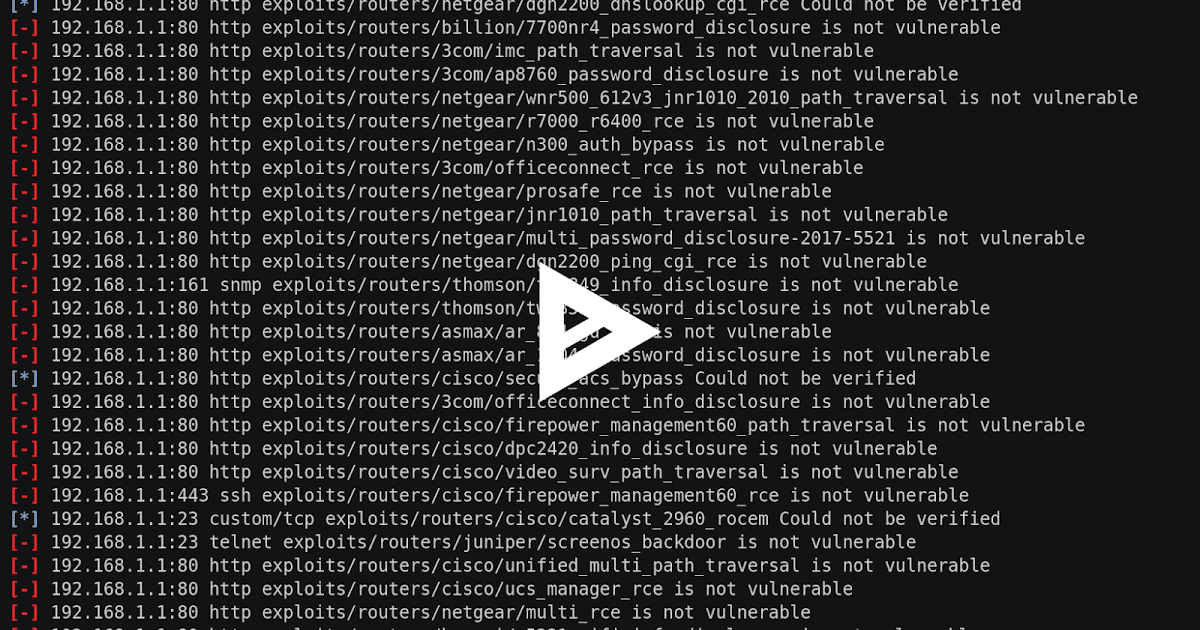
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...