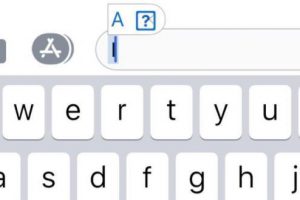
A strange text error has left some iPhone users unable to write the letter “I”. But, every time they try to use the English first-person pronoun, it gets...
Search Results For - iOS
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Critically, both OS updates address the KRACK Wi-Fi vulnerability for any devices. It is a dangerous vulnerability in the WPA2 Wi-Fi assurance standard that...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Are you a proud iPhone owner? If yes, this could freak you up. Trust me! Your iPhone has a serious privacy concern that allows iOS app developers to take your...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture...
The DumpsterFire Toolset is a modular, menu-driven, cross-platform tool for building repeatable, time-delayed, distributed security events. Easily create...