[sc name=”ad_1″] Safety checks your installed dependencies for known security vulnerabilities. By default it uses the open Python vulnerability...
Search Results For - Vulnerable
[sc name=”ad_1″] A Fuzzer For OpenRedirect Issues. Key Features : Takes a url or list of urls and fuzzes them for Open redirect issues You can...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
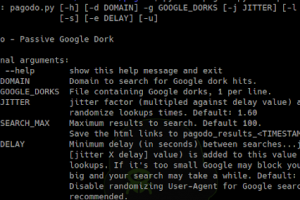
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
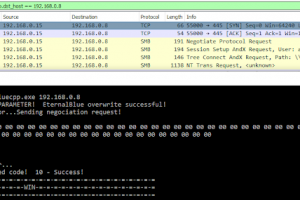
[sc name=”ad_1″] EternalBlue suite remade in C which includes: MS17-010 Exploit, EternalBlue/MS17-010 vulnerability detector, DoublePulsar detector...
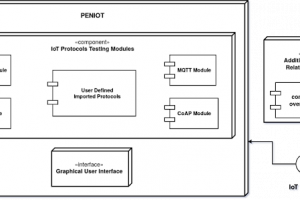
[sc name=”ad_1″] PENIOT is a penetration testing tool for Internet of Things (IoT) devices. It helps you to test/penetrate your devices by...
[sc name=”ad_1″] Tsunami is a general-purpose network security scanner with an extensible plugin system for detecting high severity vulnerabilities...
[sc name=”ad_1″] Vagrant VirtualBox Environment For Conducting An Internal Network Penetration Test. 1. Capsulecorp Pentest The Capsulecorp Pentest...