A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...
Search Results For - Vulnerable
A security enthusiast who discovered a passcode bypass vulnerability in Apple’s iOS 12 late last month has now dropped another passcode bypass bug that...
All major web browsers, including Google Chrome, Apple Safari, Microsoft Edge, Internet Explorer, and Mozilla Firefox, altogether today announced to soon...
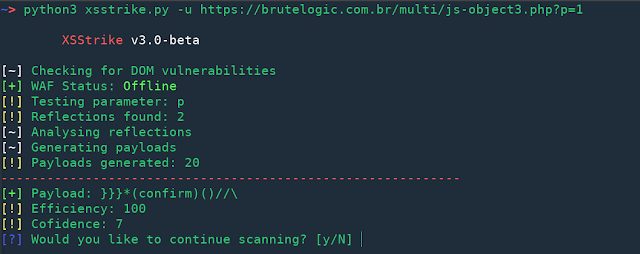
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract...
An Indian security researcher has discovered a highly critical flaw in X.Org Server package that impacts OpenBSD and most Linux distributions, including...
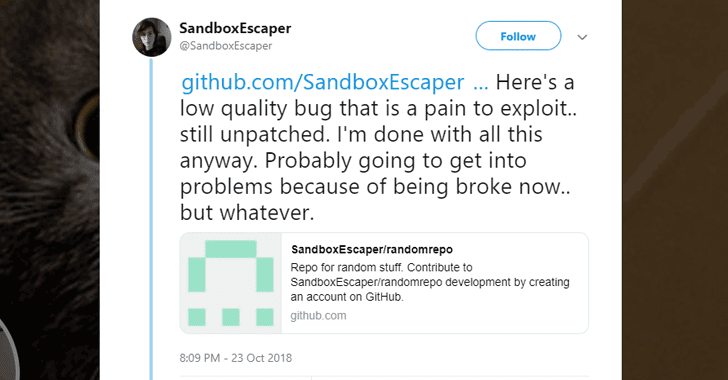
A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media...
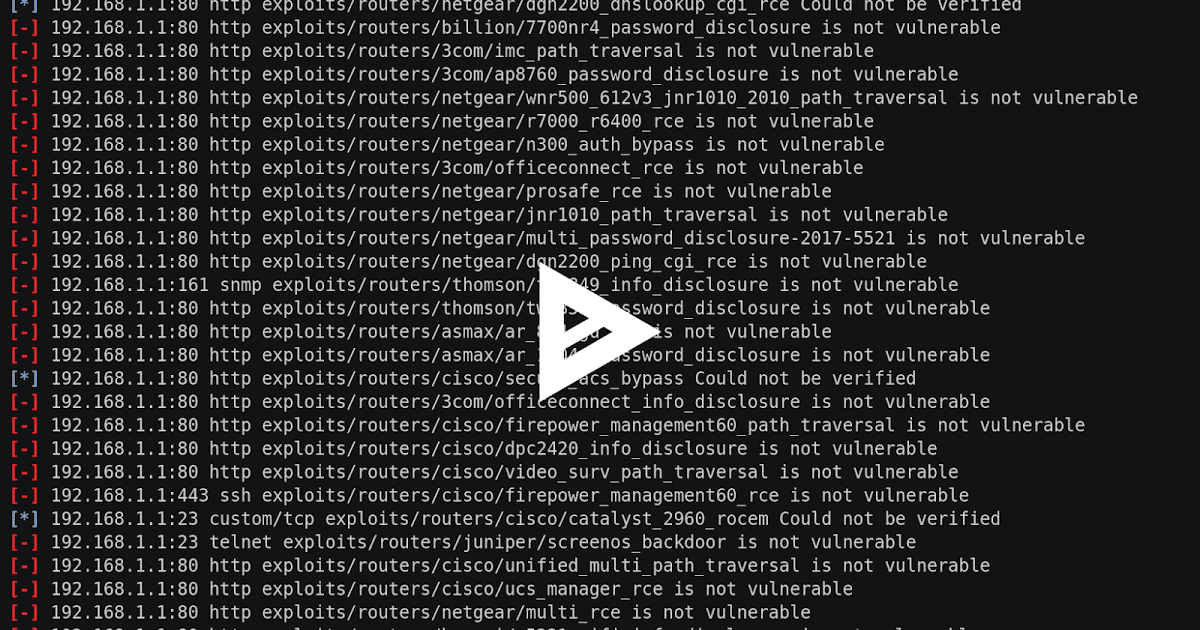
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
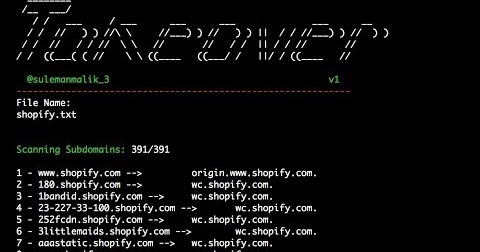
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...