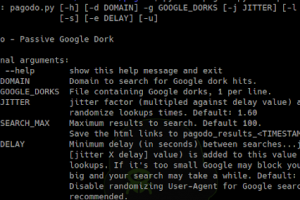
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
Search Results For - Vulnerable Application
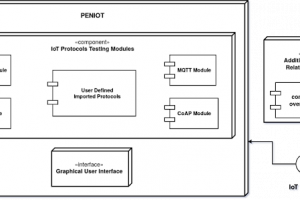
[sc name=”ad_1″] PENIOT is a penetration testing tool for Internet of Things (IoT) devices. It helps you to test/penetrate your devices by...
[sc name=”ad_1″ CLI tool and library to execute padding oracle attacks easily, with support for concurrent network requests and an elegant UI...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
[sc name=”ad_1″] Modern Denial-of-service ToolKit Main window Methods: Method Target Description SMS +PHONE SMS & CALL FLOOD NTP IP:PORT NTP...
[sc name=”ad_1″] Various cyber criminal groups and individual hackers are still exploiting a recently patched critical code execution vulnerability...
[sc name=”ad_1″] Security researchers have discovered two high-severity vulnerabilities in the SHAREit Android app that could allow attackers to...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] Beware Windows users… a new dangerous remote code execution vulnerability has been discovered in the WinRAR software...