[sc name=”ad_1″] The United States Postal Service has patched a critical security vulnerability that exposed the data of more than 60 million...
Search Results For - Visibility
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
theHarvester is a tool for gathering e-mail accounts, subdomain names, virtual hosts, open ports/ banners, and employee names from different public sources...
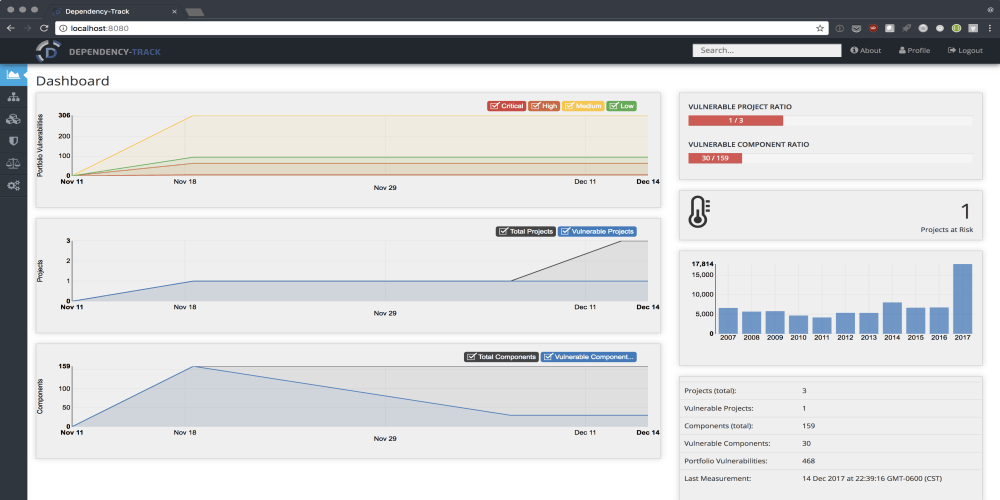
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
Infoga is a tool for gathering e-mail accounts information (ip,hostname,country,…) from different public sources (search engines, pgp key servers). Is a...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
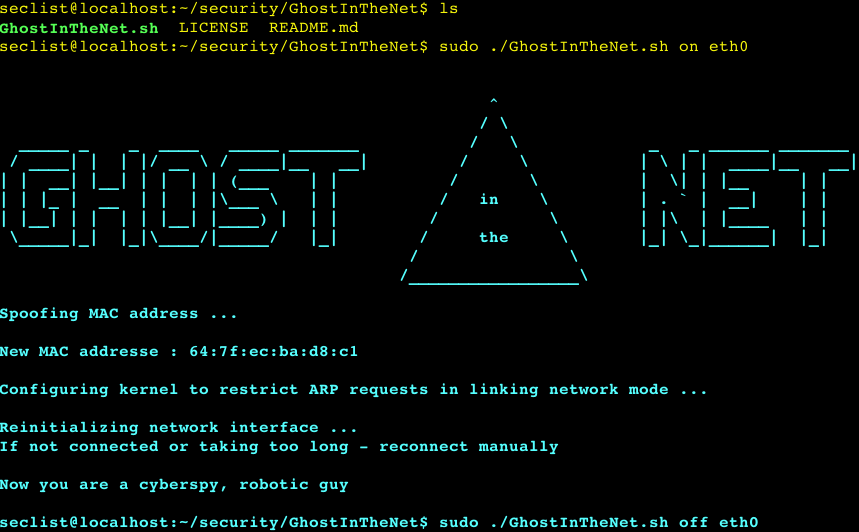
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
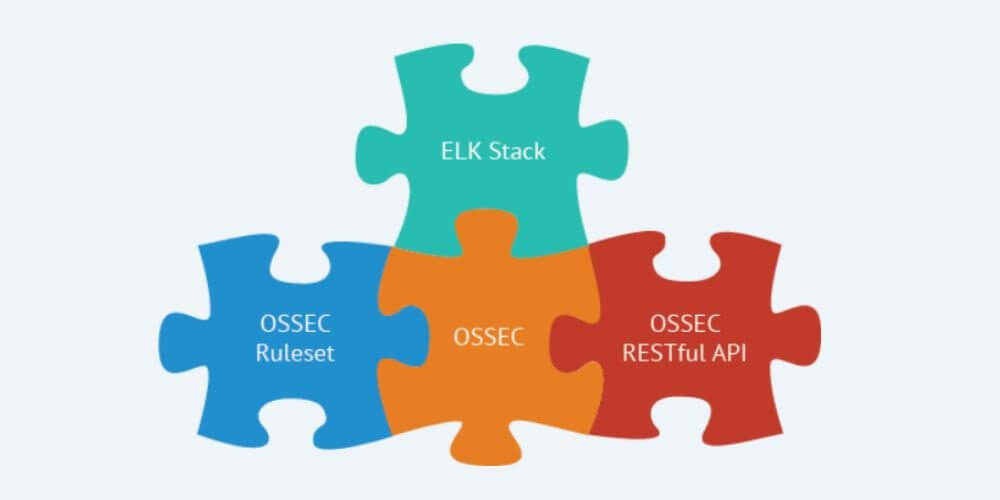
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
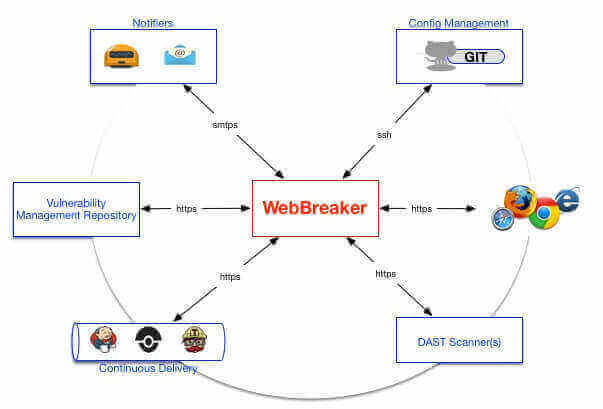
Build functional security testing, into your software development and release cycles! WebBreaker provides the capabilities to automate and centrally manage...