[sc name=”ad_1″] Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search...
Search Results For - Unix
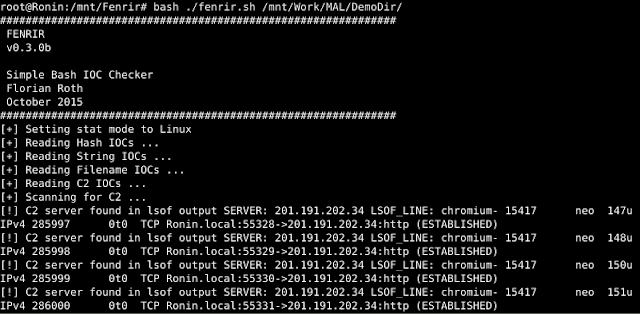
[sc name=”ad_1″] Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
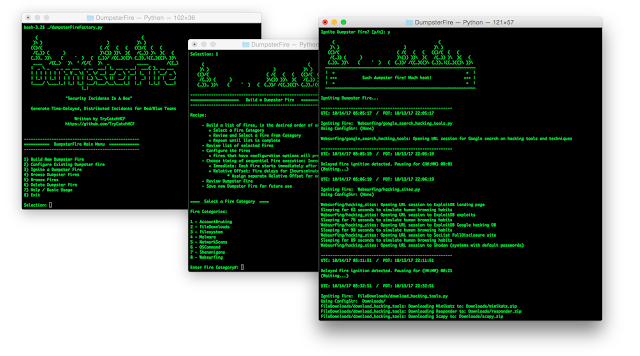
[sc name=”ad_1″] DumpsterFire Toolset – “Security Incidents In A Box!” The DumpsterFire Toolset is a modular, menu-driven, cross...
[sc name=”ad_1″] HRShell: An advanced HTTP(S) Reverse Shell built with Flask HRShell is an HTTPS/HTTP reverse shell built with flask. It’s...
[sc name=”ad_1″] SKA allows you to implement a very simple and fast karma attack. You can sniff probe requests to choice the fake AP name or, if...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
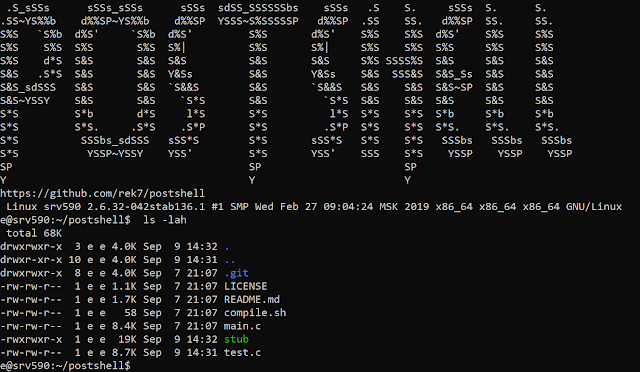
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
[sc name=”ad_1″] The popular SSH client program PuTTY has released the latest version of its software that includes security patches for 8 high...
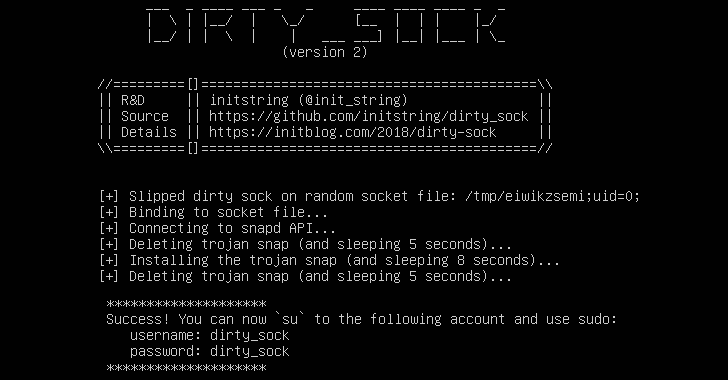
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...