[sc name=”ad_1″] Without practice, theory is dead. Applied knowledge is essential in any area, especially in cybersecurity, and practice is the...
Search Results For - Twitter
[sc name=”ad_1″] Blogpost: WARNING: you might need to restore NuGet packages and restart visual studio before compiling. If anyone knows how I can...
[sc name=”ad_1″] webscan is a browser-based network IP scanner and local IP detector. It detects IPs bound to the user/victim by listening on an...
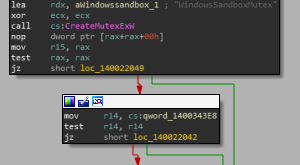
[sc name=”ad_1″] wsb-detect enables you to detect if you are running in Windows Sandbox (“WSB”). The sandbox is used by Windows...
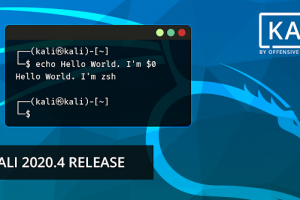
[sc name=”ad_1″] Time for another Kali Linux release! – Kali Linux 2020.4. This release has various impressive updates: ZSH is the new default...
[sc name=”ad_1″] Scripthunter is a tool that finds javascript files for a given website. To scan Google, simply run ./scripthunter.sh . Note that...
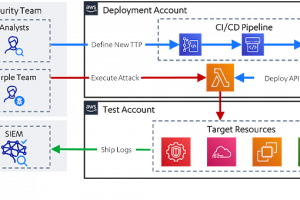
[sc name=”ad_1″] Leonidas is a framework for executing attacker actions in the cloud. It provides a YAML-based format for defining cloud attacker...
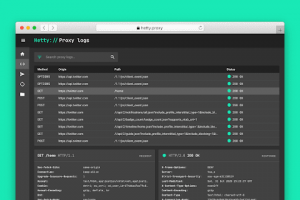
[sc name=”ad_1″] Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp...
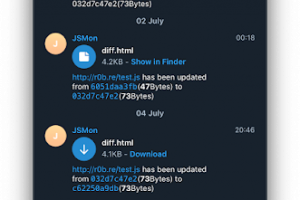
[sc name=”ad_1″] Using this script, you can configure a number of JavaScript files on websites that you want to monitor. Everytime you run this...
[sc name=”ad_1″] Easy brute forcing to whatever you want, Its magic increasing values and direct. Implementation Clone git clone Download the...