Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...
Search Results For - Threat
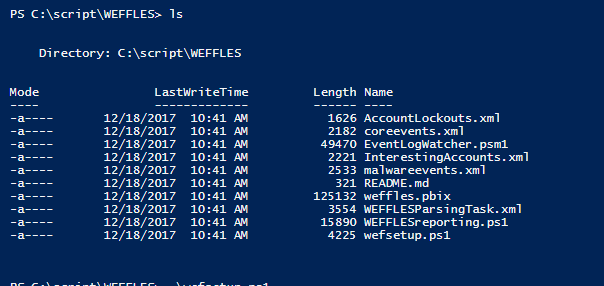
WEFFLES is designed to be small and lightweight, both for speed of getting something deployed during an Incident Response and also for the sake of being...
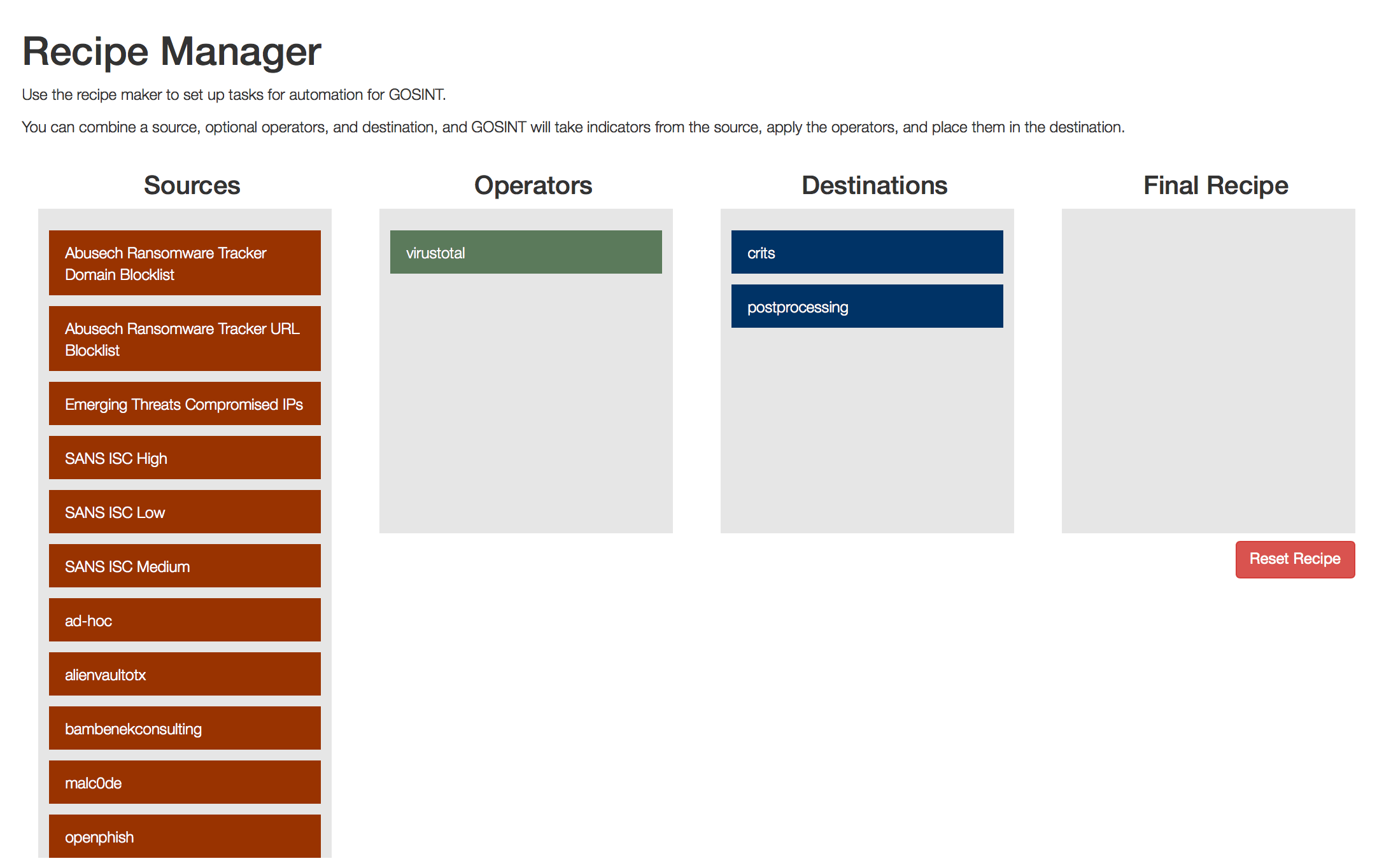
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
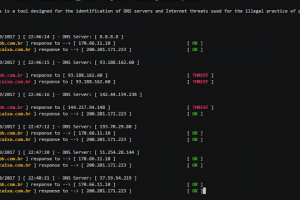
Phishruffus is a tool designed to identify threats and malicious DNS servers on the Internet that are used for the illicit practice of bank phishing. Usage: $...
Just a year after Mirai—biggest IoT-based malware that caused vast Internet outages by launching massive DDoS attacks—completed its first anniversary, security...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
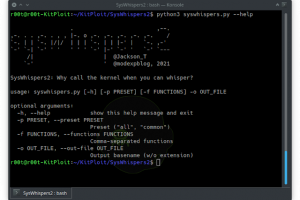
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
[sc name=”ad_1″] ByteDance-HIDS is a Cloud-Native Host-Based Intrusion Detection solution project to provide next-generation Threat Detection and...
[sc name=”ad_1″] Aura is a static analysis framework developed as a response to the ever-increasing threat of malicious packages and vulnerable...