In response to law enforcement’s increased involvement with targeting the illegal activities taking place on the Dark Web, criminals have began to use...
Search Results For - Threat
The British government has admitted publicly for the first time that it is all but certain North Korea carried out the “WannaCry” malware attack...
Exploit Pack has been designed by an experienced team of software developers and exploit writers to automate processes so penetration testers can focus on...
Many internet giants offer security measures like two-factor authentication (which you should really use) to keep your account safe from hackers. But there are...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
The DumpsterFire Toolset is a modular, menu-driven, cross-platform tool for building repeatable, time-delayed, distributed security events. Easily create...
Intelligence and Reconnaissance Package/Bundle installer. IntRec-Pack is a Bash script designed to download, install and deploy several quality OSINT, Recon...
This has been a story drifting around the internet the last few days. The victim was Elitoohey.He refined on the situation in a Reddit post, saying the bank...
A convention in Athens, Greece, Munro detailed some of the appalling security lapses Pen Test Partners found while investigating naval ships that had things...
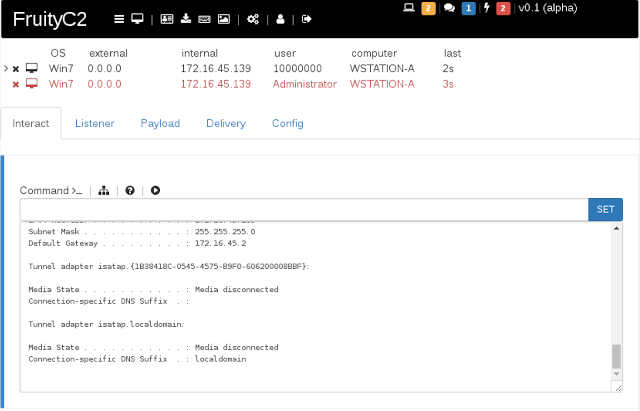
This is the initial release for FruityC2 (alpha version). Can be installed on any linux system, but the installation scripts are made for Debian based systems...