SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
Search Results For - Threat
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
Red Team Arsenal is a web/network security scanner which has the capability to scan all company’s online facing assets and provide an holistic security view of...
Author: Alex Moskov What is Litecoin? Litecoin (LTC) is a decentralized peer-to-peer cryptocurrency that was released on October 7th, 2011 and went live on...
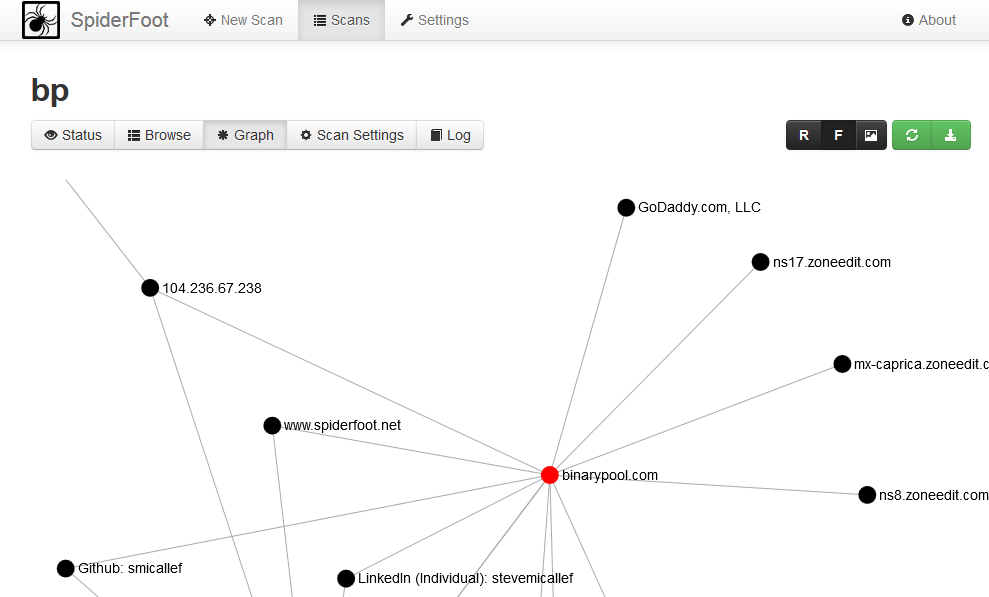
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e...
GlobaLeaks is an open-source, free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
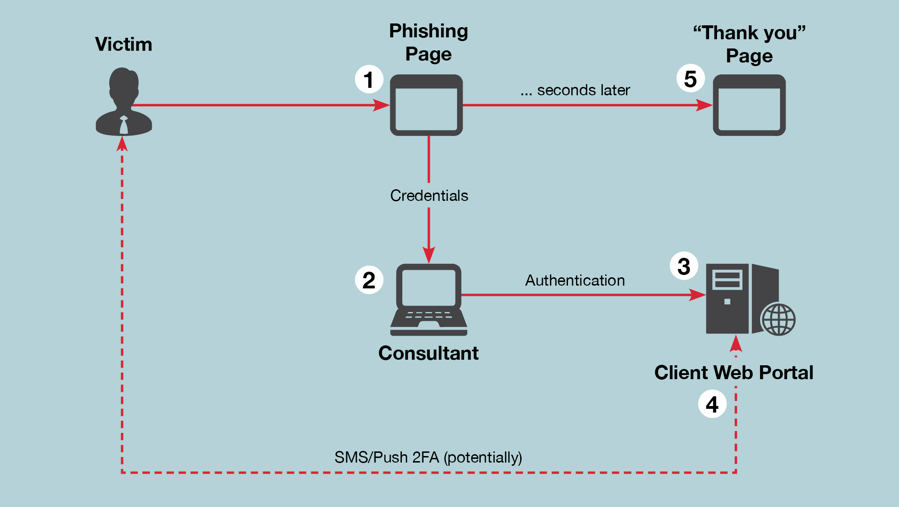
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...