[sc name=”ad_1″] Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your...
Search Results For - Threat Hunting
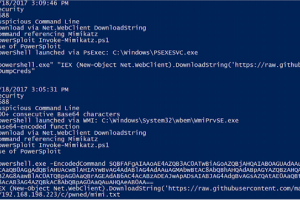
[sc name=”ad_1″] DeepBlueCLI – a PowerShell Module for Threat Hunting via Windows Event Logs Eric Conrad, Backshore Communications, LLC...
[sc name=”ad_1″] These files contain configuration for producing EDR (endpoint detection and response) data in addition to standard system logs...
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
WEFFLES is designed to be small and lightweight, both for speed of getting something deployed during an Incident Response and also for the sake of being...
[sc name=”ad_1″] RITA is an open source framework for network traffic analysis. The framework ingests Bro/Zeek Logs in TSV format, and currently...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
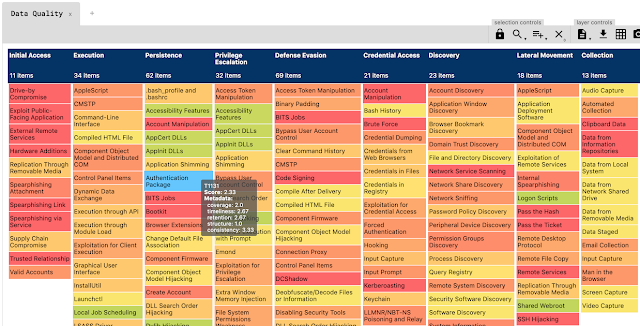
[sc name=”ad_1″] A tool to assess data quality, built on top of the awesome OSSEM project. Mission Answer the question: I want to start hunting...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] Cloud Security Operations What is Cloud Sniper? Cloud Sniper is a platform designed to manage Security Operations in cloud...