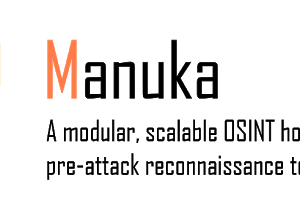[sc name=”ad_1″] These files contain configuration for producing EDR (endpoint detection and response) data in addition to standard system logs...
Search Results For - Threat Detection
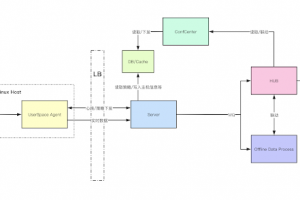
[sc name=”ad_1″] ByteDance-HIDS is a Cloud-Native Host-Based Intrusion Detection solution project to provide next-generation Threat Detection and...
[sc name=”ad_1″] Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your...
[sc name=”ad_1″] teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect...
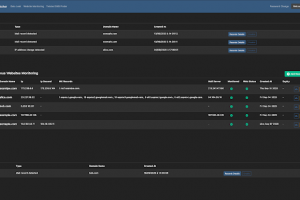
[sc name=”ad_1″] RITA is an open source framework for network traffic analysis. The framework ingests Bro/Zeek Logs in TSV format, and currently...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
[sc name=”ad_1″] Manuka is an Open-source intelligence (OSINT) honeypot that monitors reconnaissance attempts by threat actors and generates...
[sc name=”ad_1″] How do you know whether an attacker has infiltrated your network? Can you really rely on an Endpoint Detection and Response (EDR)...
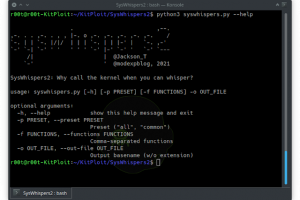
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
[sc name=”ad_1″] Aura is a static analysis framework developed as a response to the ever-increasing threat of malicious packages and vulnerable...