Hey Guys, To join HackTheBox, you will need an invite code, In this video i show you how to get an invite code for HackTheBox. Hack The Box is an online...
Search Results For - Testing
The goal of this volatility plugin is to extract a screenshot of all open X windows from a memory dump. Overview The plugin first dumps the X server memory...
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
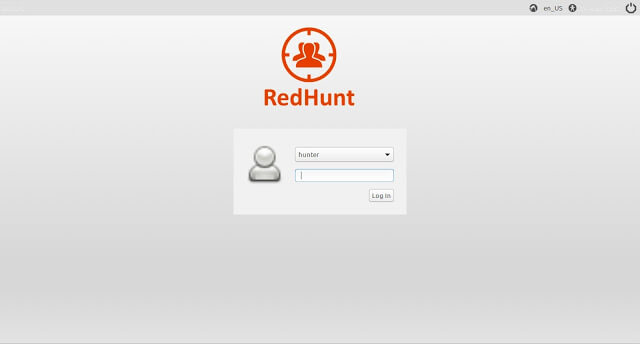
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
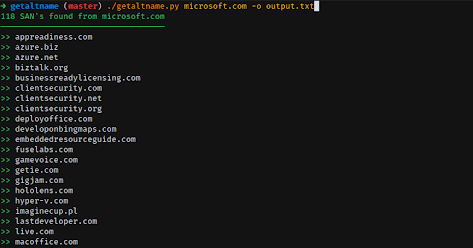
GetAltName it’s a little script that can extract Subject Alt Names for SSL Certificates directly from HTTPS web sites which can provide you with DNS...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
Raspberry Pi 3 Model B+ is now on sale for $35 (the same price as the existing Raspberry Pi 3 Model B), featuring: A 1.4GHz 64-bit quad-core ARM Cortex-A53 CPU...
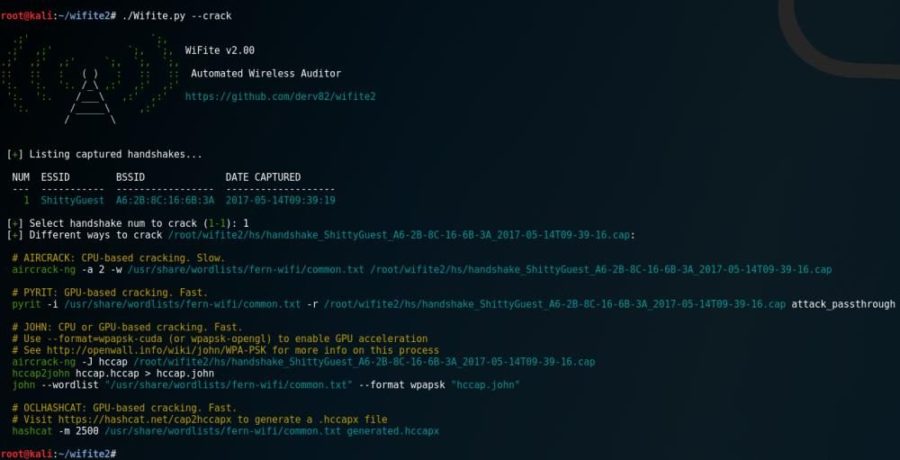
Wifite is a Python script for auditing wireless networks which aims to be the “set it and forget it” wireless auditing tool. What’s new in Wifite 2...
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP) for the...