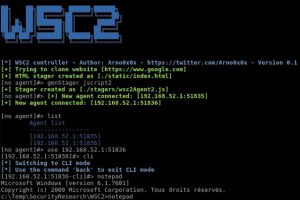
WSC2 is a PoC of using the WebSockets and a browser process to serve as a C2 communication channel between an agent, running on the target system, and a...
Search Results For - Socket
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
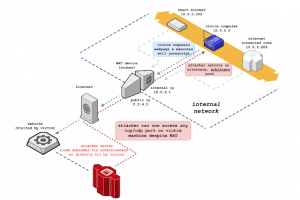
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
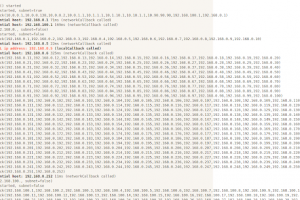
[sc name=”ad_1″] webscan is a browser-based network IP scanner and local IP detector. It detects IPs bound to the user/victim by listening on an...
[sc name=”ad_1″] Xerror is an automated penetration tool , which will helps security professionals and non professionals to automate their...
[sc name=”ad_1″] A (coverage-)guided fuzzer for dynamic language interpreters based on a custom intermediate language (“FuzzIL”) which...
[sc name=”ad_1″] Paradoxia Remote Access Tool. Features Paradoxia Console Feature Description Easy to use Paradoxia is extremely easy to use, So...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
[sc name=”ad_1″] mikrot8over: Fast exploitation tool for Mikrotik RouterOS up to 6.38.4 This is reworked original Mikrotik Exploit. Added Python 2...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...