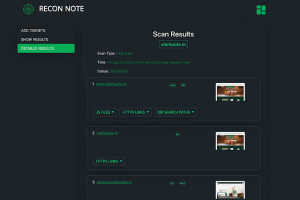
[sc name=”ad_1″] Web Application Security Recon Automation Framework It takes user input as a domain name and maximize the attack surface area by...
Search Results For - Security Automation
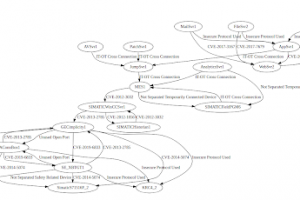
[sc name=”ad_1″] This prototype identifies security risk sources (i.e., threats and vulnerabilities) and types of attack consequences based on...
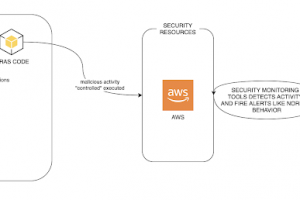
[sc name=”ad_1″] Security Incident Response Automated Simulations (SIRAS) are internal/controlled actions that provide a structured opportunity to...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] Linux evil toolkit is a framework that aims to centralize, standardize and simplify the use of various security tools for pentest...
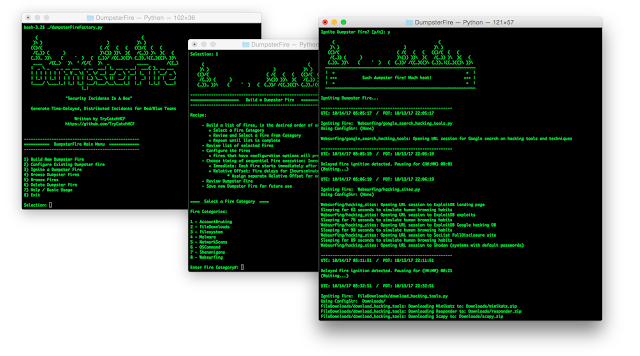
[sc name=”ad_1″] DumpsterFire Toolset – “Security Incidents In A Box!” The DumpsterFire Toolset is a modular, menu-driven, cross...
[sc name=”ad_1″] A security researcher has discovered a severe vulnerability in the popular, open source event-driven platform StackStorm that...
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
The DumpsterFire Toolset is a modular, menu-driven, cross-platform tool for building repeatable, time-delayed, distributed security events. Easily create...