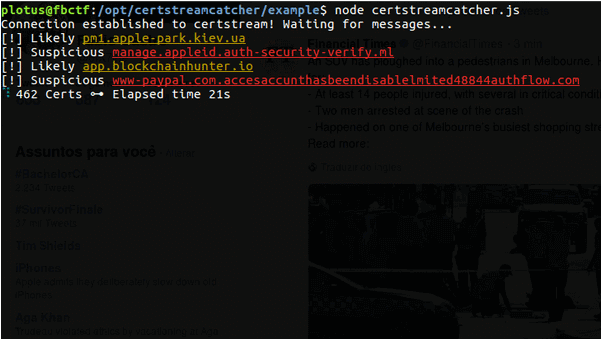
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
Search Results For - Secure
A script for installing and automatically configuring DNSCrypt on Linux-based systems. Description DNSCrypt is a protocol for securing communications between a...
Christmas is the time of the year where gift cards are on the rise. As per The National Retail Federation, people in the U.S are expected to spend $27.6...
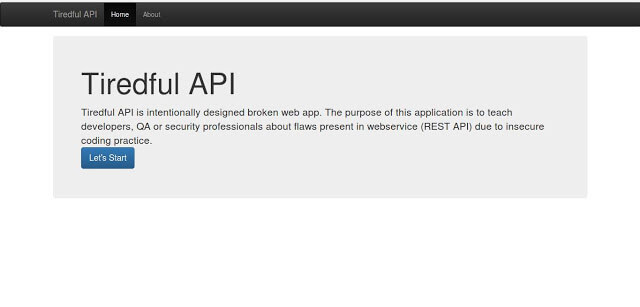
Tiredful API is intentionally designed broken app. The aim of this web app is to teach developers, QA or security professionals about flaws present in...
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
The U.S. federal officials have arrested two hackers who have pleaded guilty to computer-crimes charges for creating and distributing Mirai botnet that...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
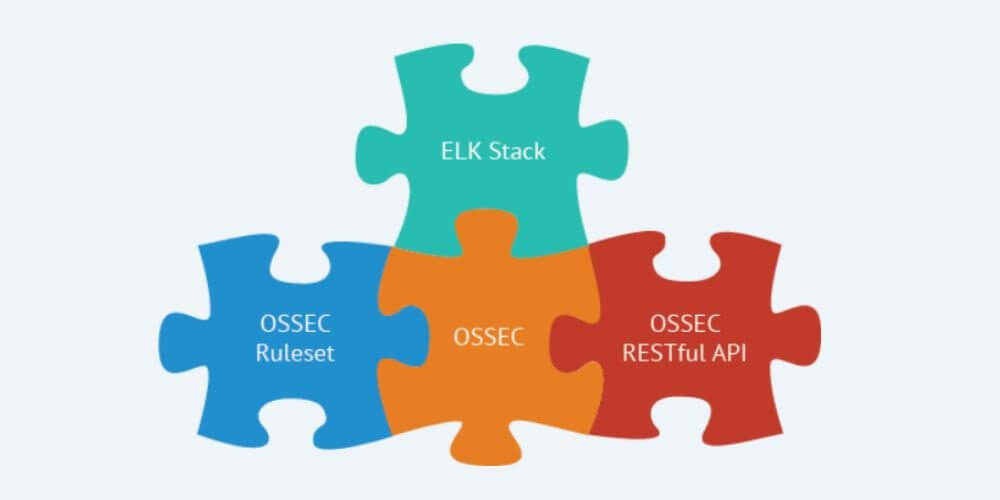
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
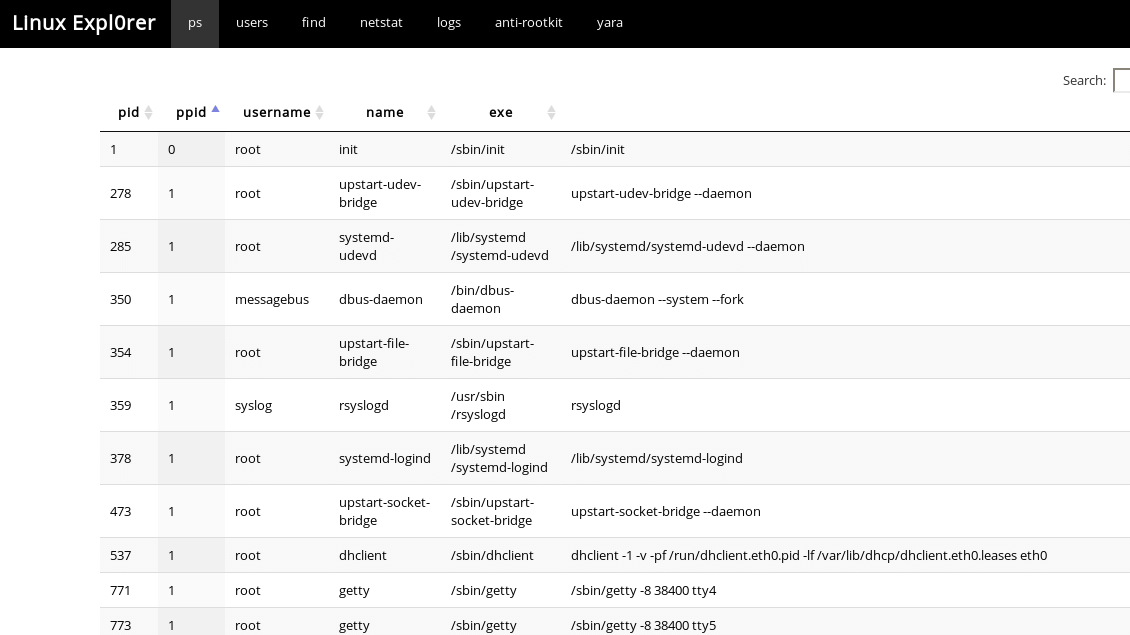
Easy-to-use live forensics toolbox for Linux endpoints written in Python & Flask. Capabilities ps View full process list Inspect process memory map &...
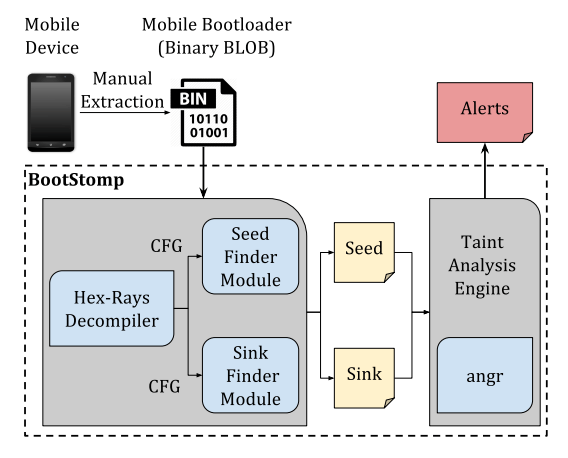
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...