Spectre & Meltdown Checker A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs...
Search Results For - Secure
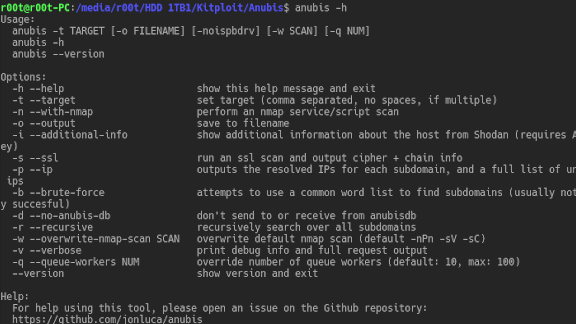
Anubis is a subdomain enumeration and information gathering tool. Anubis collates data from a variety of sources, including HackerTarget, DNSDumpster, x509...
At last, Wi-Fi security — or lack of — is about to get its day in the sun. The Wi-Fi Alliance, an industry body made up of device makers including...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
It’s time to learn how to renew its OS because researcher James Bercegay has found a dozen models possess a hard-coded backdoor. The backdoor, lets anyone log...
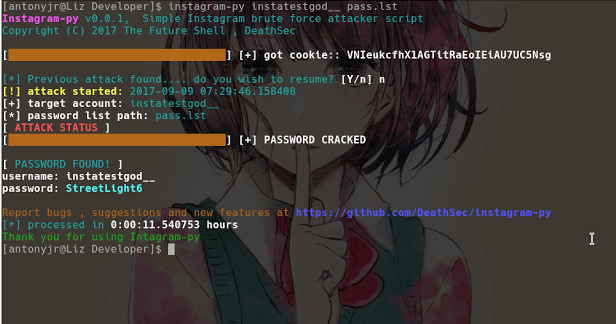
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
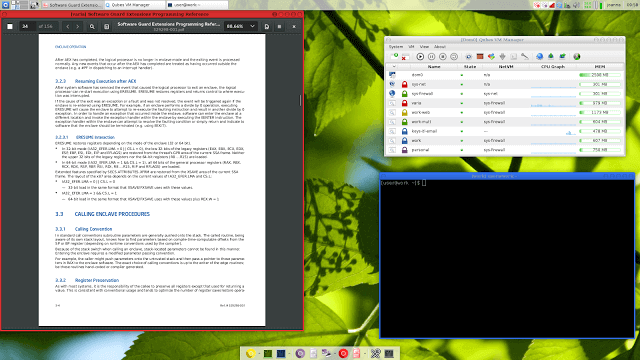
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
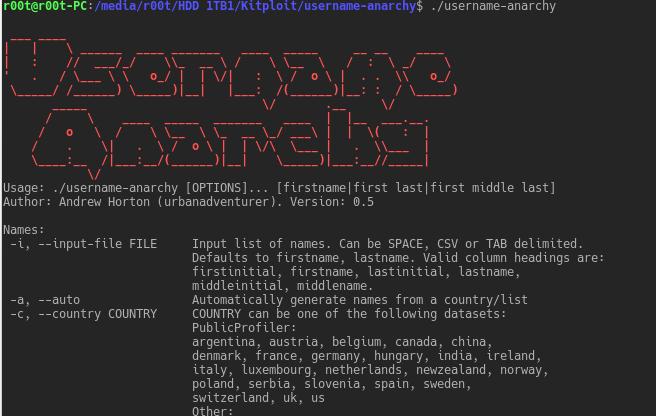
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...
The PowerUpSQL module includes functions that support SQL Server discovery, auditing for common weak configurations, and privilege escalation on scale. It is...