[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
Search Results For - Secure Coding
[sc name=”ad_1″] Aura is a static analysis framework developed as a response to the ever-increasing threat of malicious packages and vulnerable...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
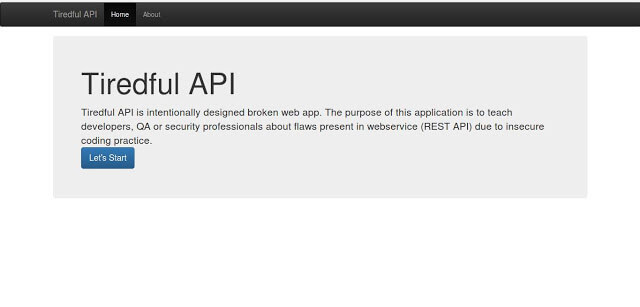
Tiredful API is intentionally designed broken app. The aim of this web app is to teach developers, QA or security professionals about flaws present in...
[sc name=”ad_1″] Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1...
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
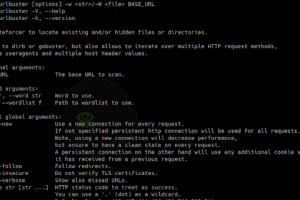
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
[sc name=”ad_1″] kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in the CIS...
[sc name=”ad_1″] Working and learning have gone remote, and we have to come to terms with this new reality. Nowadays, several organizations allow...
[sc name=”ad_1″] Set of tools for creating/injecting payload into images. Useful references for better understanding of pixload and its use-cases:...