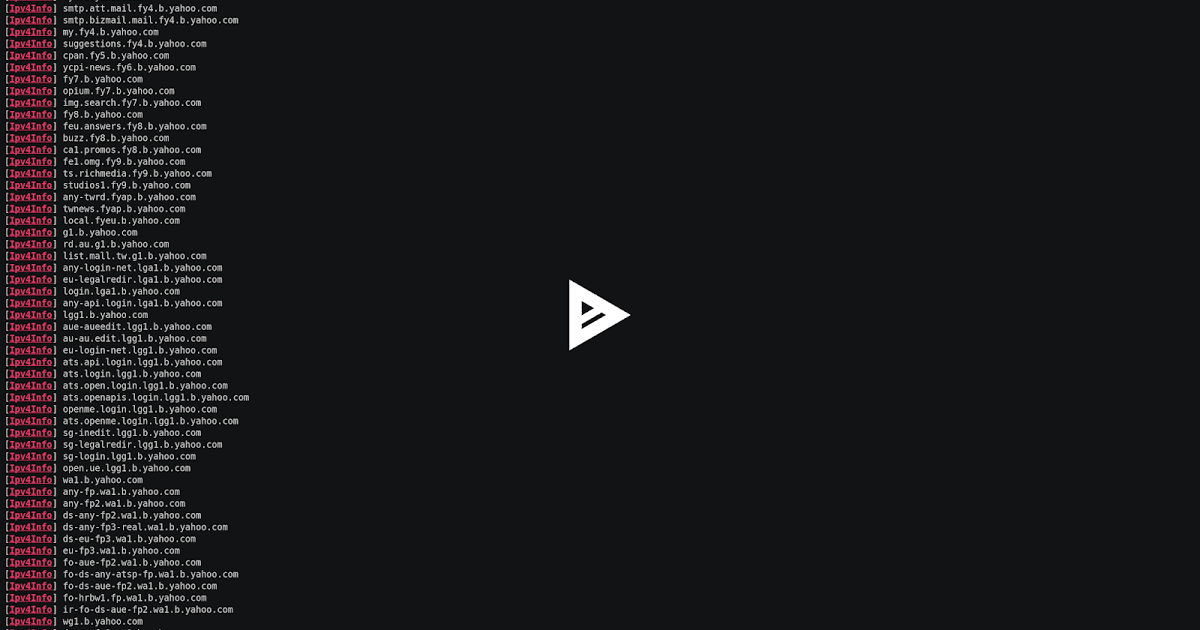
SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
Search Results For - Scan
pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
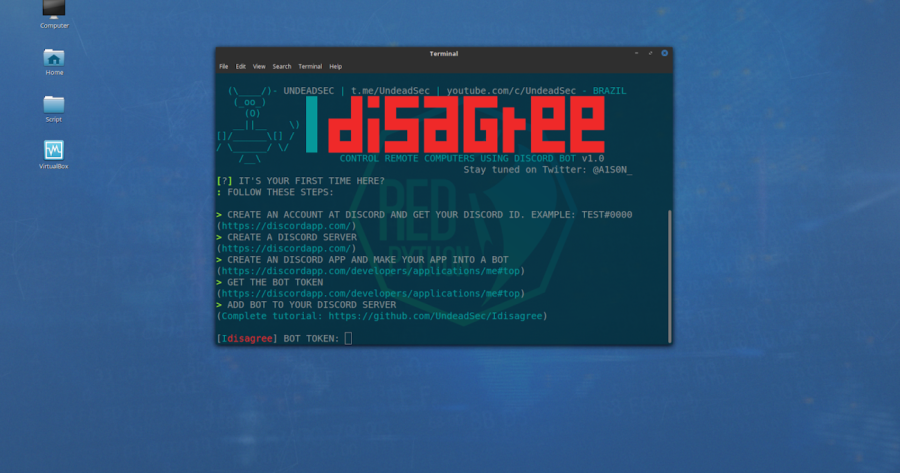
Control remote computers using discord bot and python 3. [ ! ] If your target is a windows system, you may want to compile your payload. Do this with py2exe or...
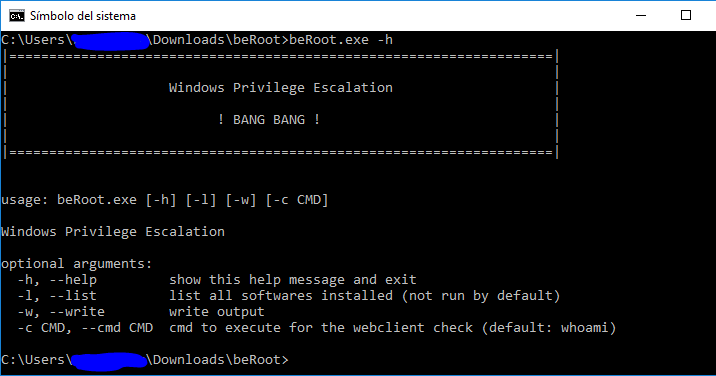
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
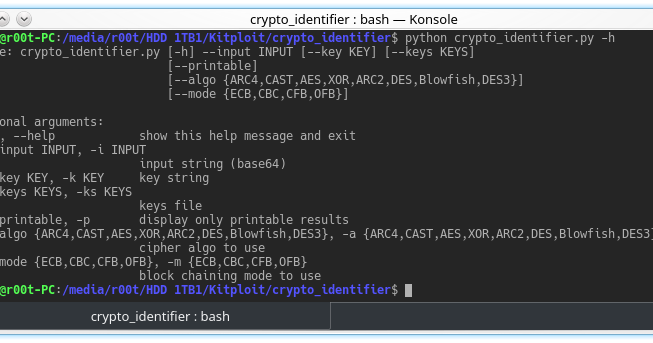
Crypto tool for pentest and ctf : try to uncipher data using multiple algorithms and block chaining modes. Usefull for a quick check on unknown cipher text and...
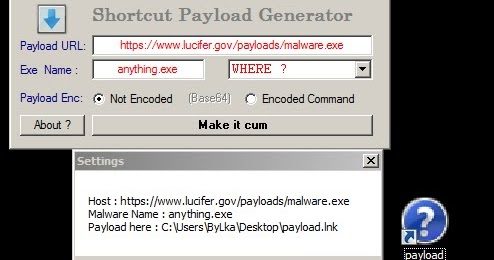
Making FUD Shortcut (.lnk) payloads with LNK-KISSER to remote execute malicious code. Shortcut-Payload-Generator Exploiting Powershell to make ShortCut...
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
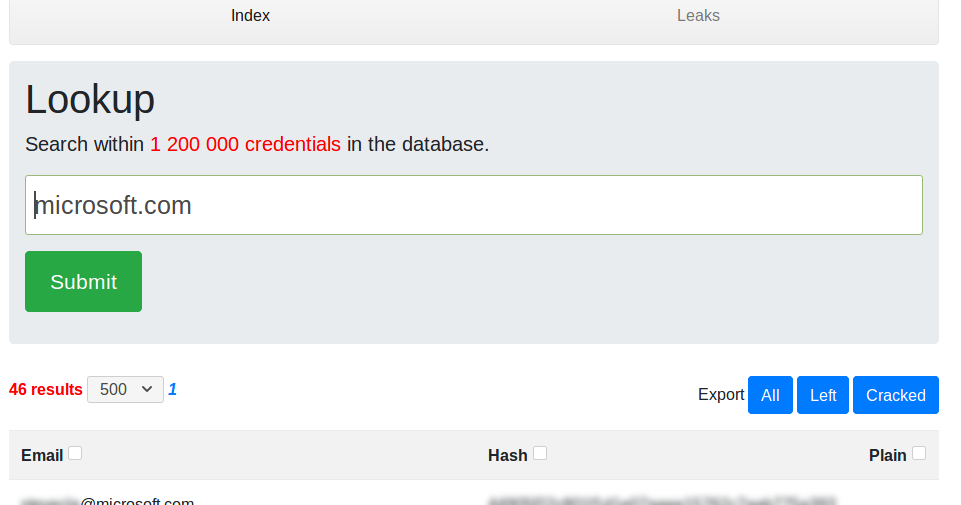
LeakScraper is an efficient set of tools to process and visualize huge text files containing credentials. These tools are designed to help...