Run PowerShell with dlls only. Does not require access to powershell.exe as it uses powershell automation dlls. dll mode: Usage: rundll32 PowerShdll,main...
Search Results For - Restrictions
[sc name=”ad_1″] Umbrella is an Android mobile app developed by Security First that provides human rights defenders with the information on what to...
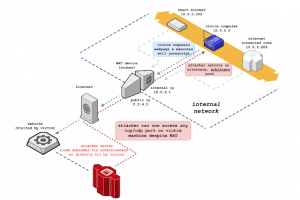
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
[sc name=”ad_1″] The HUD is new interface that provides the functionality of ZAP directly in the browser. Learn more: Blog: Hacking with a Heads Up...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] Mística is a tool that allows to embed data into application layer protocol fields, with the goal of establishing a bi-directional...
[sc name=”ad_1″] Santa is a binary whitelisting/blacklisting system for macOS. It consists of a kernel extension (or a system extension on macOS 10...
[sc name=”ad_1″] Spyse is a cybersecurity search engine for finding technical information about different internet entities, business data, and...
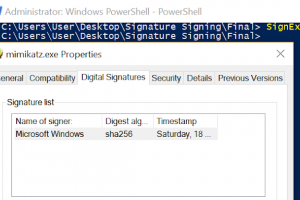
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
[sc name=”ad_1″] Google has recently released the first beta version of Android Q, the next upcoming version of Google’s popular mobile...