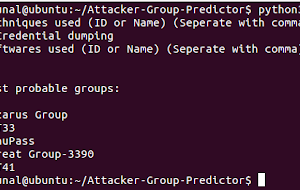
[sc name=”ad_1″] The tool predicts attacker groups from techniques and softwares used. It searches based on the MITRE ATT&CK framework How it...
Search Results For - Requirements
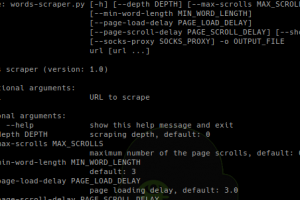
[sc name=”ad_1″] Selenium based web scraper to generate passwords list. Installation # Download Firefox webdriver from $ tar xzf geckodriver...
[sc name=”ad_1″] How it works Scan common ports Send a TCP Syn packet to the destination on the defined port, if the port is open, use an nmap scan...
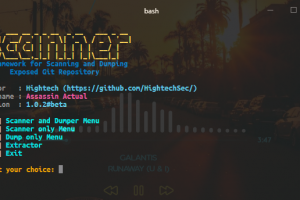
[sc name=”ad_1″] This tool can scan websites with open .git repositories for Bug Hunting/ Pentesting Purposes and can dump the content of the .git...
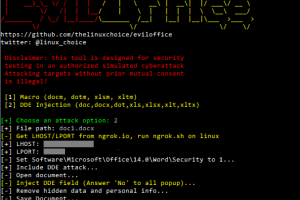
[sc name=”ad_1″] Win python script to inject Macro and DDE code into Excel and Word documents (reverse shell) Features: Inject malicious Macro on...
[sc name=”ad_1″] GitMonitor is a Github scanning system to look for leaked sensitive information based on rules. I know that there are a lot of...
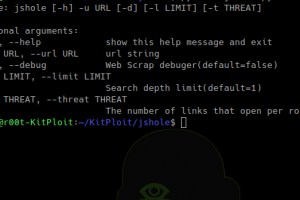
[sc name=”ad_1″] A JavaScript components vulnerability scanner, based on RetireJS. Why use JShole instead of RetireJS? By default, RetireJS only...
[sc name=”ad_1″] The Forerunner library is a fast, lightweight, and extensible networking library created to aid in the development of robust...
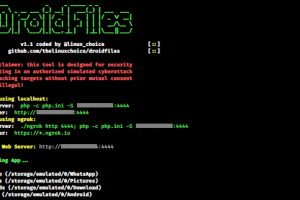
[sc name=”ad_1″] Get files from Android directories, internal and external storage (Pictures, Downloads, Whatsapp, Videos, …) Legal...
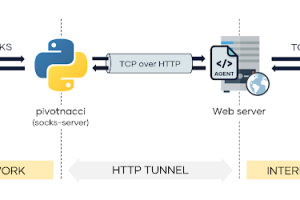
[sc name=”ad_1″] Pivot into the internal network by deploying HTTP agents. Pivotnacci allows you to create a socks server which communicates with...