Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
Search Results For - Remote Access
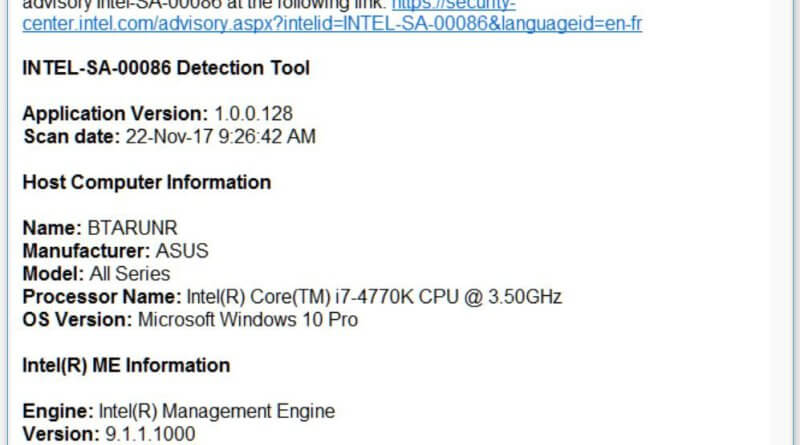
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
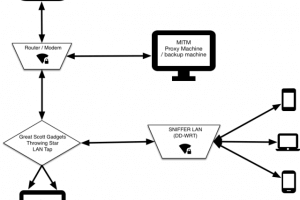
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
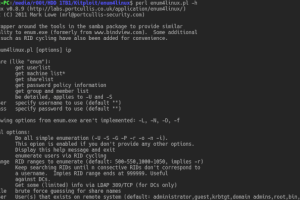
A Linux alternative to enum.exe for enumerating data from Windows and Samba hosts. Enum4linux is a tool for enumerating information from Windows and Samba...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
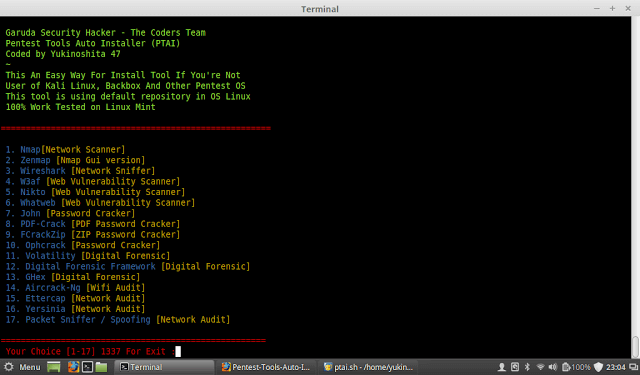
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...