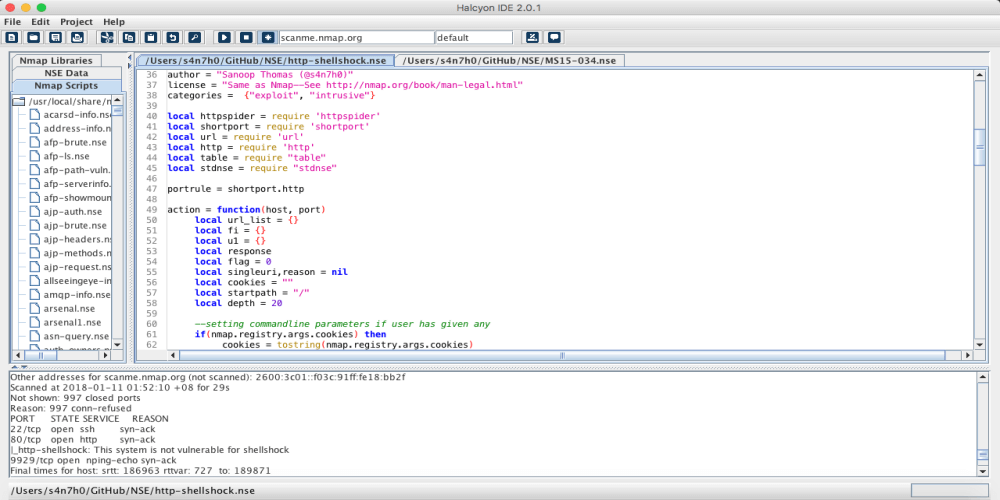
Halcyon IDE lets you quickly and easily develop scripts for performing advanced scans on applications and infrastructures with a range from recon to...
Search Results For - Recon
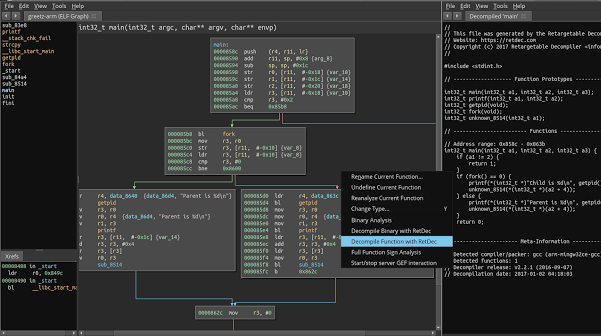
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
BtleJuice is a complete framework to perform Man-in-the-Middle attacks on Bluetooth Smart devices (also known as Bluetooth Low Energy). It is composed of: an...
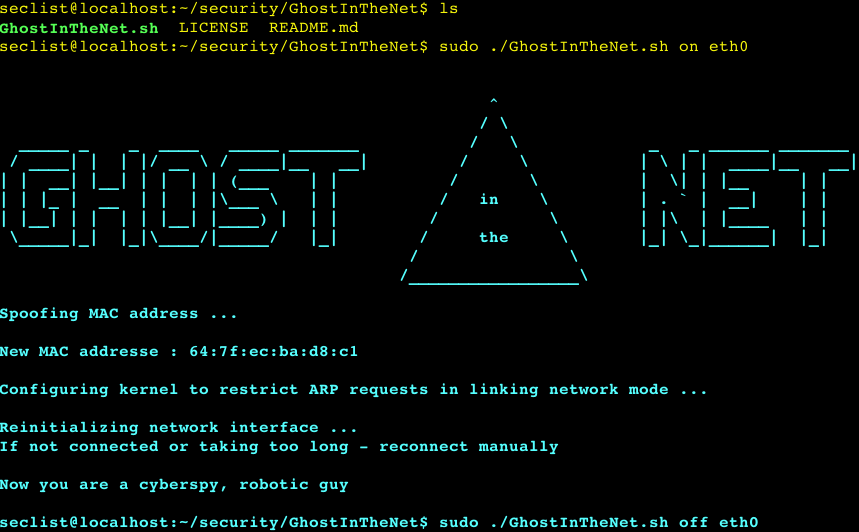
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
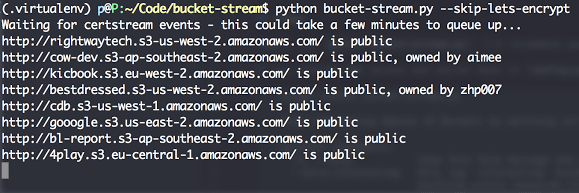
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and...
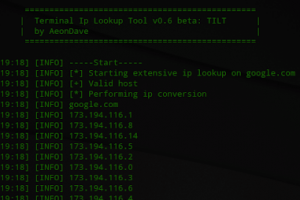
Tilt: Terminal ip lookup tool, is an easy and simple open source tool implemented in Python for ip/host passive reconnaissance. It’s very handy for first...
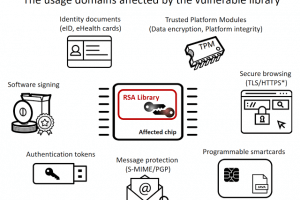
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
“I don’t remember if my data has been sold to the dark web or where this goes,” she said. “I keep getting letters from Kohl’s, from Macy’s, from Old Navy...
AWSBucketDump is a tool to quickly enumerate AWS S3 buckets to look for loot. It’s similar to a subdomain bruteforcer but is made specifically for S3...