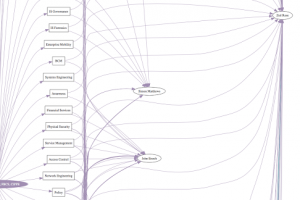
An OSINT tool that allows you to draw out relationships between people on LinkedIn via endorsements/skills. Check out the example (digraph), which is based on...
Search Results For - Python 3
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
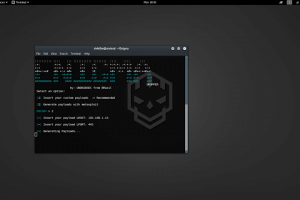
Enigma is a Multiplatform payload dropper. Run git clone cd Enigma python enigma.py or python3 enigma3.py Prerequisites python 2.7 for enigma.py python 3.x for...
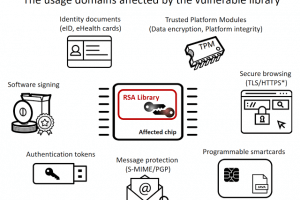
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
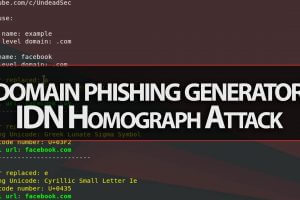
Hey Guys, In this video i show you a great tool for unicode domain phishing generation for IDN Homograph Attack. EvilURL: CLONE git clone RUNNING cd EvilURL...
Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as...
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
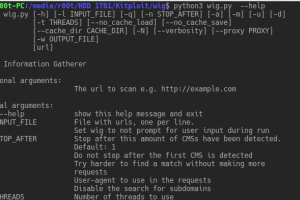
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
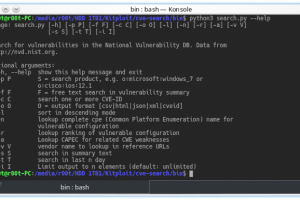
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...