[sc name=”ad_1″] How do you know whether an attacker has infiltrated your network? Can you really rely on an Endpoint Detection and Response (EDR)...
Search Results For - Protection
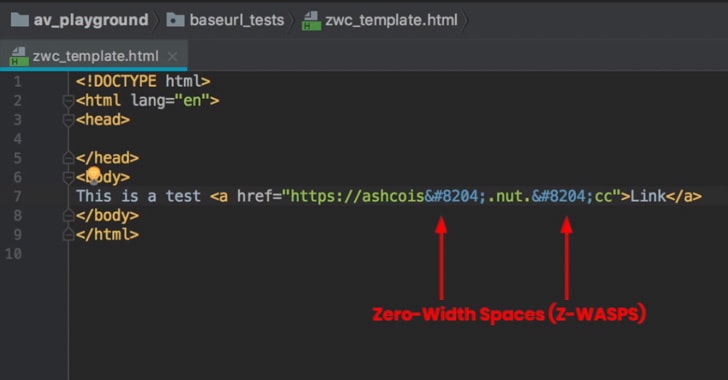
[sc name=”ad_1″] Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in...
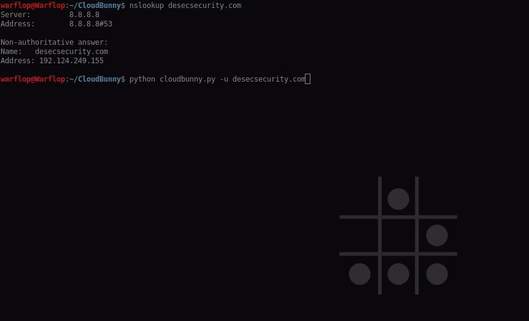
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
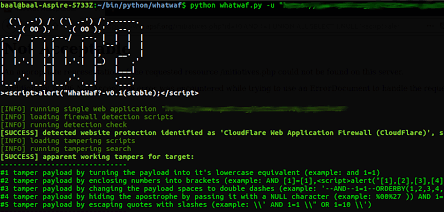
WhatWaf is an advanced firewall detection tool who’s goal is to give you the idea of “There’s a WAF?”. WhatWaf works by detecting a...
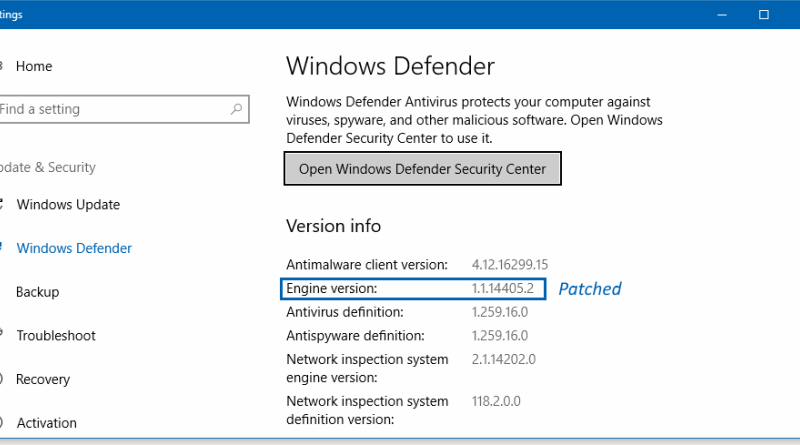
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
Many internet giants offer security measures like two-factor authentication (which you should really use) to keep your account safe from hackers. But there are...
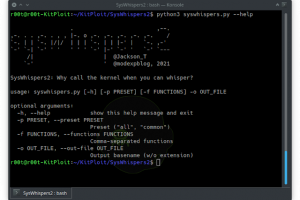
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
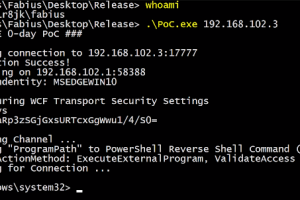
[sc name=”ad_1″] Credential Dumping Tool for SolarWinds Orion Blog post: Credit to @asolino, @gentilkiwi, and @skelsec for helping me figuring out...
[sc name=”ad_1″] Swiss army knife Webserver in Golang. Keep simple like the python SimpleHTTPServer but with many features. Usage Help $ ...
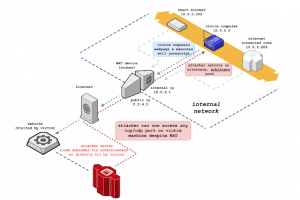
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...